Introducing
IntroducingWindowsServer2016_ebook
IntroducingWindowsServer2016_ebook
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Following on from that, you should begin to focus on implementing time-bound privileges; that is, a<br />
user can request privileges that will expire after a predefined period of time. This means that there<br />
does not need to be actual administrators, as such, because the users can request the access they<br />
need, be approved, and perform the necessary tasks. This concept is based on Microsoft Identity<br />
Manager and functions provided by JEA.<br />
You also should implement multifactor authentication for privileged access to further mitigate attacks<br />
on the systems. You can do this by using token-based security or call-back or smart cards. Next, you<br />
can begin to implement JEA. JEA is simple in principle because it specifies that you grant the very<br />
minimal amount of privileges to an account that are needed to perform the given function. We will<br />
talk about JEA in more detail later in this chapter.<br />
Further securing domain controllers is the next step, and you will finish by implementing threat<br />
detection via Advanced Threat Analytics (ATA). ATA provides the ability to detect abnormal behavior<br />
in your systems and make you aware of them quickly. It does this by profiling your user’s behavior<br />
and establishing what that user’s normal patterns are. If the user does something outside this normal<br />
pattern, ATA will alert you. ATA is far more advanced than this simple explanation implies. To learn<br />
more about it, go to http://aka.ms/ata.<br />
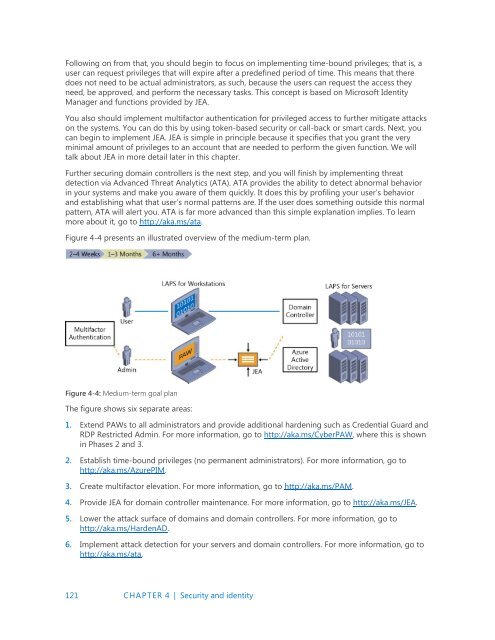
Figure 4-4 presents an illustrated overview of the medium-term plan.<br />
Figure 4-4: Medium-term goal plan<br />
The figure shows six separate areas:<br />
1. Extend PAWs to all administrators and provide additional hardening such as Credential Guard and<br />
RDP Restricted Admin. For more information, go to http://aka.ms/CyberPAW, where this is shown<br />
in Phases 2 and 3.<br />
2. Establish time-bound privileges (no permanent administrators). For more information, go to<br />
http://aka.ms/AzurePIM.<br />
3. Create multifactor elevation. For more information, go to http://aka.ms/PAM.<br />
4. Provide JEA for domain controller maintenance. For more information, go to http://aka.ms/JEA.<br />
5. Lower the attack surface of domains and domain controllers. For more information, go to<br />
http://aka.ms/HardenAD.<br />
6. Implement attack detection for your servers and domain controllers. For more information, go to<br />
http://aka.ms/ata.<br />
121 CHAPTER 4 | Security and identity