Release Notes: Version E.10.37 Software
Release Notes: Version E.10.37 Software
Release Notes: Version E.10.37 Software
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Clarifications<br />
General Switch Traffic Security Guideline<br />
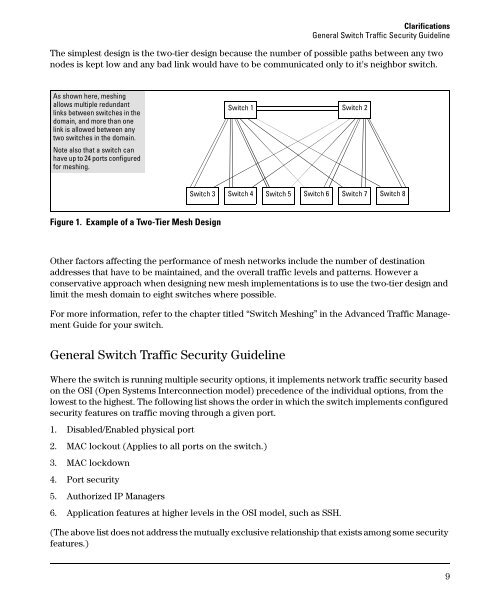
The simplest design is the two-tier design because the number of possible paths between any two<br />
nodes is kept low and any bad link would have to be communicated only to it's neighbor switch.<br />
As shown here, meshing<br />
allows multiple redundant<br />
links between switches in the<br />
domain, and more than one<br />
link is allowed between any<br />
two switches in the domain.<br />
Note also that a switch can<br />
have up to 24 ports configured<br />
for meshing.<br />
Switch 1 Switch 2<br />
Switch 3 Switch 4 Switch 5 Switch 6 Switch 7 Switch 8<br />
Figure 1. Example of a Two-Tier Mesh Design<br />
Other factors affecting the performance of mesh networks include the number of destination<br />
addresses that have to be maintained, and the overall traffic levels and patterns. However a<br />
conservative approach when designing new mesh implementations is to use the two-tier design and<br />
limit the mesh domain to eight switches where possible.<br />
For more information, refer to the chapter titled “Switch Meshing” in the Advanced Traffic Management<br />
Guide for your switch.<br />
General Switch Traffic Security Guideline<br />
Where the switch is running multiple security options, it implements network traffic security based<br />
on the OSI (Open Systems Interconnection model) precedence of the individual options, from the<br />
lowest to the highest. The following list shows the order in which the switch implements configured<br />
security features on traffic moving through a given port.<br />
1. Disabled/Enabled physical port<br />
2. MAC lockout (Applies to all ports on the switch.)<br />
3. MAC lockdown<br />
4. Port security<br />
5. Authorized IP Managers<br />
6. Application features at higher levels in the OSI model, such as SSH.<br />
(The above list does not address the mutually exclusive relationship that exists among some security<br />
features.)<br />
9