syssec_red_book
syssec_red_book
syssec_red_book
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
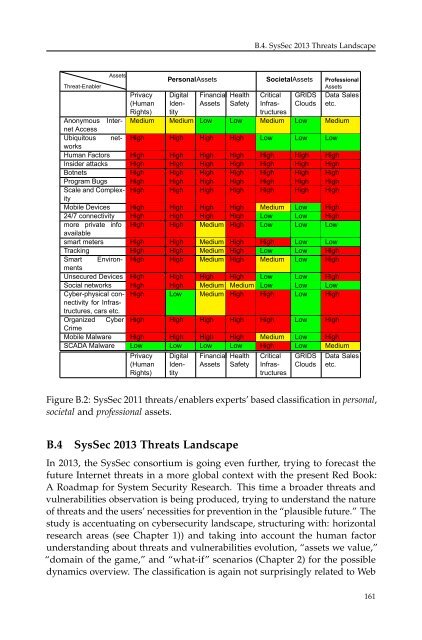
B.4. SysSec 2013 Threats LandscapeThreat-EnablerAssetsPrivacy(HumanRights)PersonalAssets SocietalAssets ProfessionalAssetsDigitalIdentityFinancialAssetsHealthSafetyGRIDSCloudsData Salesetc.CriticalInfrastructuresAnonymous InternetMedium Medium Low Low Medium Low MediumAccessUbiquitous networksHigh High High High Low Low LowHuman Factors High High High High High High HighInsider attacks High High High High High High HighBotnets High High High High High High HighProgram Bugs High High High High High High HighScale and ComplexityHigh High High High High High HighMobile Devices High High High High Medium Low High24/7 connectivity High High High High Low Low Highmore private info High High Medium High Low Low Lowavailablesmart meters High High Medium High High Low LowTracking High High Medium High Low Low HighSmart EnvironmentsHigh High Medium High Medium Low HighUnsecu<strong>red</strong> Devices High High High High Low Low HighSocial networks High High Medium Medium Low Low LowCyber-physical connectivityHigh Low Medium High High Low Highfor Infras-tructures, cars etc.Organized Cyber High High High High High Low HighCrimeMobile Malware High High High High Medium Low HighSCADA Malware Low Low Low Low High Low MediumPrivacy(HumanRights)DigitalIdentityFinancialAssetsHealthSafetyCriticalInfrastructuresGRIDSCloudsData Salesetc.Figure B.2: SysSec 2011 threats/enablers experts’ based classification in personal,societal and professional assets.B.4 SysSec 2013 Threats LandscapeIn 2013, the SysSec consortium is going even further, trying to forecast thefuture Internet threats in a more global context with the present Red Book:A Roadmap for System Security Research. This time a broader threats andvulnerabilities observation is being produced, trying to understand the natureof threats and the users’ necessities for prevention in the “plausible future.” Thestudy is accentuating on cybersecurity landscape, structuring with: horizontalresearch areas (see Chapter 1)) and taking into account the human factorunderstanding about threats and vulnerabilities evolution, “assets we value,”“domain of the game,” and “what-if” scenarios (Chapter 2) for the possibledynamics overview. The classification is again not surprisingly related to Web161