Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
netsh advfirewall firewall set rule name=”<strong>Windows</strong> Remote Management (HTTP-In)” new<br />
enable=yes<br />
If an error message “A specific value is not valid” appears, verify <strong>the</strong> rule’s name. The alternative<br />
approach is to enter <strong>the</strong> netsh context, followed by <strong>the</strong> advfirewall context, and <strong>the</strong> firewall context. In<br />
<strong>the</strong> firewall context, repeat <strong>the</strong> command for <strong>the</strong> specific rule.<br />
2.6.2 Source Firewall<br />
When WinRM is executed <strong>with</strong> <strong>the</strong> quickconfig option, it creates a default firewall rule that allows<br />
inbound WinRM traffic. The firewall rule automatically sets <strong>the</strong> required port (80 or 5985) depending on<br />
<strong>the</strong> WinRM version. Configuring WinRM locally on sources is discouraged as using Group Policy is more<br />
manageable.<br />
2.6.2.1 WinRM 2.0<br />
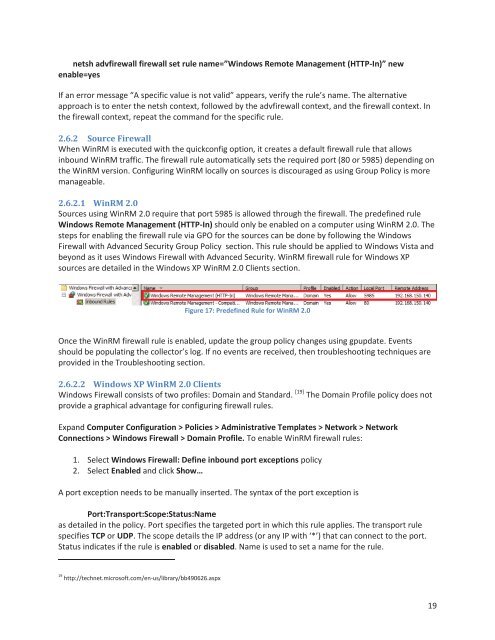
Sources using WinRM 2.0 require that port 5985 is allowed through <strong>the</strong> firewall. The predefined rule<br />
<strong>Windows</strong> Remote Management (HTTP-In) should only be enabled on a computer using WinRM 2.0. The<br />
steps for enabling <strong>the</strong> firewall rule via GPO for <strong>the</strong> sources can be done by following <strong>the</strong> <strong>Windows</strong><br />
Firewall <strong>with</strong> Advanced Security Group Policy section. This rule should be applied to <strong>Windows</strong> Vista and<br />
beyond as it uses <strong>Windows</strong> Firewall <strong>with</strong> Advanced Security. WinRM firewall rule for <strong>Windows</strong> XP<br />
sources are detailed in <strong>the</strong> <strong>Windows</strong> XP WinRM 2.0 Clients section.<br />
Figure 17: Predefined Rule for WinRM 2.0<br />
Once <strong>the</strong> WinRM firewall rule is enabled, update <strong>the</strong> group policy changes using gpupdate. <strong>Event</strong>s<br />
should be populating <strong>the</strong> collector’s log. If no events are received, <strong>the</strong>n troubleshooting techniques are<br />
provided in <strong>the</strong> Troubleshooting section.<br />
2.6.2.2 <strong>Windows</strong> XP WinRM 2.0 Clients<br />
<strong>Windows</strong> Firewall consists of two profiles: Domain and Standard. [19] The Domain Profile policy does not<br />
provide a graphical advantage for configuring firewall rules.<br />
Expand Computer Configuration > Policies > Administrative Templates > Network > Network<br />
Connections > <strong>Windows</strong> Firewall > Domain Profile. To enable WinRM firewall rules:<br />
1. Select <strong>Windows</strong> Firewall: Define inbound port exceptions policy<br />
2. Select Enabled and click Show…<br />
A port exception needs to be manually inserted. The syntax of <strong>the</strong> port exception is<br />
Port:Transport:Scope:Status:Name<br />
as detailed in <strong>the</strong> policy. Port specifies <strong>the</strong> targeted port in which this rule applies. The transport rule<br />
specifies TCP or UDP. The scope details <strong>the</strong> IP address (or any IP <strong>with</strong> ‘*’) that can connect to <strong>the</strong> port.<br />
Status indicates if <strong>the</strong> rule is enabled or disabled. Name is used to set a name for <strong>the</strong> rule.<br />
19 http://technet.microsoft.com/en-us/library/bb490626.aspx<br />
19