Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
3.2 Security <strong>Log</strong> in <strong>Windows</strong> XP<br />
By default, <strong>Windows</strong> XP does not audit security activities. [41] There are several different audit policies<br />
which can be enabled to audit security logs.<br />
Expand Computer Configuration > Policies > <strong>Windows</strong> Settings > Security Settings > Local Policies ><br />
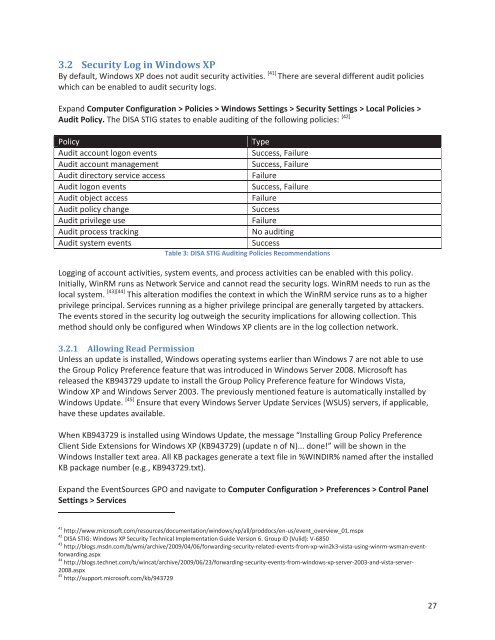
Audit Policy. The DISA STIG states to enable auditing of <strong>the</strong> following policies: [42]<br />
Policy<br />
Audit account logon events<br />
Audit account management<br />
Audit directory service access<br />
Audit logon events<br />
Audit object access<br />
Audit policy change<br />
Audit privilege use<br />
Audit process tracking<br />
Audit system events<br />
Type<br />
Success, Failure<br />
Success, Failure<br />
Failure<br />
Success, Failure<br />
Failure<br />
Success<br />
Failure<br />
No auditing<br />
Success<br />
Table 3: DISA STIG Auditing Policies Recommendations<br />
<strong>Log</strong>ging of account activities, system events, and process activities can be enabled <strong>with</strong> this policy.<br />
Initially, WinRM runs as Network Service and cannot read <strong>the</strong> security logs. WinRM needs to run as <strong>the</strong><br />
local system. [43][44] This alteration modifies <strong>the</strong> context in which <strong>the</strong> WinRM service runs as to a higher<br />
privilege principal. Services running as a higher privilege principal are generally targeted by attackers.<br />
The events stored in <strong>the</strong> security log outweigh <strong>the</strong> security implications for allowing collection. This<br />
method should only be configured when <strong>Windows</strong> XP clients are in <strong>the</strong> log collection network.<br />
3.2.1 Allowing Read Permission<br />
Unless an update is installed, <strong>Windows</strong> operating systems earlier than <strong>Windows</strong> 7 are not able to use<br />
<strong>the</strong> Group Policy Preference feature that was introduced in <strong>Windows</strong> Server 2008. Microsoft has<br />
released <strong>the</strong> KB943729 update to install <strong>the</strong> Group Policy Preference feature for <strong>Windows</strong> Vista,<br />
Window XP and <strong>Windows</strong> Server 2003. The previously mentioned feature is automatically installed by<br />
<strong>Windows</strong> Update. [45] Ensure that every <strong>Windows</strong> Server Update Services (WSUS) servers, if applicable,<br />
have <strong>the</strong>se updates available.<br />
When KB943729 is installed using <strong>Windows</strong> Update, <strong>the</strong> message “Installing Group Policy Preference<br />
Client Side Extensions for <strong>Windows</strong> XP (KB943729) (update n of N)... done!” will be shown in <strong>the</strong><br />
<strong>Windows</strong> Installer text area. All KB packages generate a text file in %WINDIR% named after <strong>the</strong> installed<br />
KB package number (e.g., KB943729.txt).<br />
Expand <strong>the</strong> <strong>Event</strong>Sources GPO and navigate to Computer Configuration > Preferences > Control Panel<br />
Settings > Services<br />
41 http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/event_overview_01.mspx<br />
42 DISA STIG: <strong>Windows</strong> XP Security Technical Implementation Guide Version 6. Group ID (Vulid): V-6850<br />
43 http://blogs.msdn.com/b/wmi/archive/2009/04/06/forwarding-security-related-events-from-xp-win2k3-vista-using-winrm-wsman-eventforwarding.aspx<br />
44 http://blogs.technet.com/b/wincat/archive/2009/06/23/forwarding-security-events-from-windows-xp-server-2003-and-vista-server-<br />
2008.aspx<br />
45 http://support.microsoft.com/kb/943729<br />
27