Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
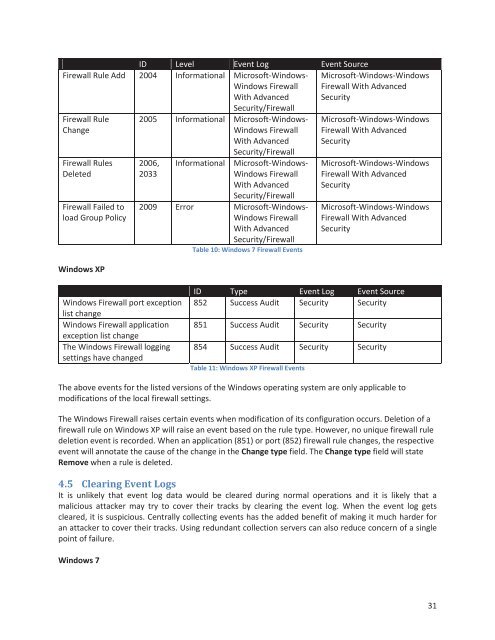
ID Level <strong>Event</strong> <strong>Log</strong> <strong>Event</strong> Source<br />
Firewall Rule Add 2004 Informational Microsoft-<strong>Windows</strong>-<br />
<strong>Windows</strong> Firewall<br />
With Advanced<br />
Security/Firewall<br />
Firewall Rule<br />
Change<br />
Firewall Rules<br />
Deleted<br />
Firewall Failed to<br />
load Group Policy<br />
<strong>Windows</strong> XP<br />
2005 Informational Microsoft-<strong>Windows</strong>-<br />
<strong>Windows</strong> Firewall<br />
With Advanced<br />
Security/Firewall<br />
2006,<br />
2033<br />
Informational<br />
Microsoft-<strong>Windows</strong>-<br />
<strong>Windows</strong> Firewall<br />
With Advanced<br />
Security/Firewall<br />
2009 Error Microsoft-<strong>Windows</strong>-<br />
<strong>Windows</strong> Firewall<br />
With Advanced<br />
Security/Firewall<br />
Table 10: <strong>Windows</strong> 7 Firewall <strong>Event</strong>s<br />
Microsoft-<strong>Windows</strong>-<strong>Windows</strong><br />
Firewall With Advanced<br />
Security<br />
Microsoft-<strong>Windows</strong>-<strong>Windows</strong><br />
Firewall With Advanced<br />
Security<br />
Microsoft-<strong>Windows</strong>-<strong>Windows</strong><br />
Firewall With Advanced<br />
Security<br />
Microsoft-<strong>Windows</strong>-<strong>Windows</strong><br />
Firewall With Advanced<br />
Security<br />
<strong>Windows</strong> Firewall port exception<br />
list change<br />
<strong>Windows</strong> Firewall application<br />
exception list change<br />
The <strong>Windows</strong> Firewall logging<br />
settings have changed<br />
ID Type <strong>Event</strong> <strong>Log</strong> <strong>Event</strong> Source<br />
852 Success Audit Security Security<br />
851 Success Audit Security Security<br />
854 Success Audit Security Security<br />
Table 11: <strong>Windows</strong> XP Firewall <strong>Event</strong>s<br />
The above events for <strong>the</strong> listed versions of <strong>the</strong> <strong>Windows</strong> operating system are only applicable to<br />
modifications of <strong>the</strong> local firewall settings.<br />
The <strong>Windows</strong> Firewall raises certain events when modification of its configuration occurs. Deletion of a<br />
firewall rule on <strong>Windows</strong> XP will raise an event based on <strong>the</strong> rule type. However, no unique firewall rule<br />
deletion event is recorded. When an application (851) or port (852) firewall rule changes, <strong>the</strong> respective<br />
event will annotate <strong>the</strong> cause of <strong>the</strong> change in <strong>the</strong> Change type field. The Change type field will state<br />
Remove when a rule is deleted.<br />
4.5 Clearing <strong>Event</strong> <strong>Log</strong>s<br />
It is unlikely that event log data would be cleared during normal operations and it is likely that a<br />
malicious attacker may try to cover <strong>the</strong>ir tracks by clearing <strong>the</strong> event log. When <strong>the</strong> event log gets<br />
cleared, it is suspicious. Centrally collecting events has <strong>the</strong> added benefit of making it much harder for<br />
an attacker to cover <strong>the</strong>ir tracks. Using redundant collection servers can also reduce concern of a single<br />
point of failure.<br />
<strong>Windows</strong> 7<br />
31