Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
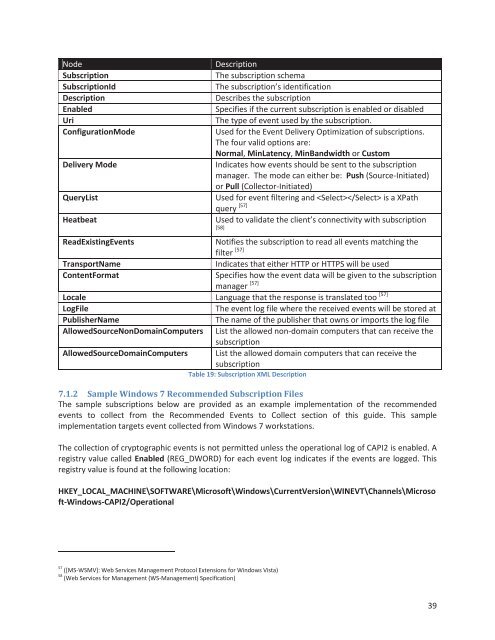
Node<br />
Subscription<br />
SubscriptionId<br />
Description<br />
Enabled<br />
Uri<br />
ConfigurationMode<br />
Delivery Mode<br />
QueryList<br />
Heatbeat<br />
Description<br />
The subscription schema<br />
The subscription’s identification<br />
Describes <strong>the</strong> subscription<br />
Specifies if <strong>the</strong> current subscription is enabled or disabled<br />
The type of event used by <strong>the</strong> subscription.<br />
Used for <strong>the</strong> <strong>Event</strong> Delivery Optimization of subscriptions.<br />
The four valid options are:<br />
Normal, MinLatency, MinBandwidth or Custom<br />
Indicates how events should be sent to <strong>the</strong> subscription<br />
manager. The mode can ei<strong>the</strong>r be: Push (Source-Initiated)<br />
or Pull (Collector-Initiated)<br />
Used for event filtering and is a XPath<br />
query [57]<br />
Used to validate <strong>the</strong> client’s connectivity <strong>with</strong> subscription<br />
[58]<br />
ReadExisting<strong>Event</strong>s<br />
Notifies <strong>the</strong> subscription to read all events matching <strong>the</strong><br />
filter [57]<br />
TransportName<br />
Indicates that ei<strong>the</strong>r HTTP or HTTPS will be used<br />
ContentFormat<br />
Specifies how <strong>the</strong> event data will be given to <strong>the</strong> subscription<br />
manager [57]<br />
Locale Language that <strong>the</strong> response is translated too [57]<br />
<strong>Log</strong>File<br />
The event log file where <strong>the</strong> received events will be stored at<br />
PublisherName<br />
The name of <strong>the</strong> publisher that owns or imports <strong>the</strong> log file<br />
AllowedSourceNonDomainComputers List <strong>the</strong> allowed non-domain computers that can receive <strong>the</strong><br />
subscription<br />
AllowedSourceDomainComputers List <strong>the</strong> allowed domain computers that can receive <strong>the</strong><br />
subscription<br />
Table 19: Subscription XML Description<br />
7.1.2 Sample <strong>Windows</strong> 7 Recommended Subscription Files<br />
The sample subscriptions below are provided as an example implementation of <strong>the</strong> recommended<br />
events to collect from <strong>the</strong> Recommended <strong>Event</strong>s to Collect section of this guide. This sample<br />
implementation targets event collected from <strong>Windows</strong> 7 workstations.<br />
The collection of cryptographic events is not permitted unless <strong>the</strong> operational log of CAPI2 is enabled. A<br />
registry value called Enabled (REG_DWORD) for each event log indicates if <strong>the</strong> events are logged. This<br />
registry value is found at <strong>the</strong> following location:<br />
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\<strong>Windows</strong>\CurrentVersion\WINEVT\Channels\Microso<br />
ft-<strong>Windows</strong>-CAPI2/Operational<br />
57 ([MS-WSMV]: Web Services Management Protocol Extensions for <strong>Windows</strong> Vista)<br />
58 (Web Services for Management (WS-Management) Specification)<br />
39