Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
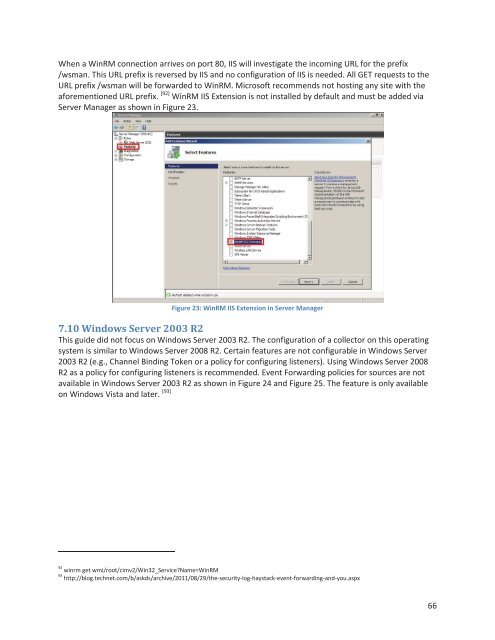
When a WinRM connection arrives on port 80, IIS will investigate <strong>the</strong> incoming URL for <strong>the</strong> prefix<br />
/wsman. This URL prefix is reversed by IIS and no configuration of IIS is needed. All GET requests to <strong>the</strong><br />
URL prefix /wsman will be forwarded to WinRM. Microsoft recommends not hosting any site <strong>with</strong> <strong>the</strong><br />
aforementioned URL prefix. [92] WinRM IIS Extension is not installed by default and must be added via<br />
Server Manager as shown in Figure 23.<br />
Figure 23: WinRM IIS Extension in Server Manager<br />
7.10 <strong>Windows</strong> Server 2003 R2<br />
This guide did not focus on <strong>Windows</strong> Server 2003 R2. The configuration of a collector on this operating<br />
system is similar to <strong>Windows</strong> Server 2008 R2. Certain features are not configurable in <strong>Windows</strong> Server<br />
2003 R2 (e.g., Channel Binding Token or a policy for configuring listeners). Using <strong>Windows</strong> Server 2008<br />
R2 as a policy for configuring listeners is recommended. <strong>Event</strong> Forwarding policies for sources are not<br />
available in <strong>Windows</strong> Server 2003 R2 as shown in Figure 24 and Figure 25. The feature is only available<br />
on <strong>Windows</strong> Vista and later. [93]<br />
92 winrm get wmi/root/cimv2/Win32_Service?Name=WinRM<br />
93 http://blog.technet.com/b/askds/archive/2011/08/29/<strong>the</strong>-security-log-haystack-event-forwarding-and-you.aspx<br />
66