Risico’s van een gevirtualiseerde IT-omgeving
Risico's van een gevirtualiseerde IT-omgeving - Vurore
Risico's van een gevirtualiseerde IT-omgeving - Vurore
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
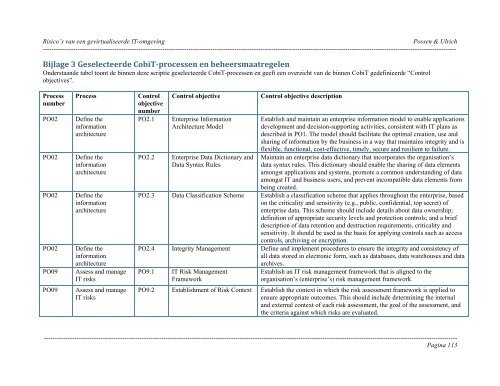
<strong>Risico’s</strong> <strong>van</strong> <strong>een</strong> <strong>gevirtualiseerde</strong> <strong>IT</strong>-<strong>omgeving</strong> Possen & Ulrich----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Bijlage 3 Geselecteerde CobiTprocessen en beheersmaatregelenOnderstaande tabel toont de binnen deze scriptie geselecteerde CobiT-processen en geeft <strong>een</strong> overzicht <strong>van</strong> de binnen CobiT gedefinieerde “Controlobjectives”.ProcessnumberPO02PO02PO02PO02PO09PO09ProcessDefine theinformationarchitectureDefine theinformationarchitectureDefine theinformationarchitectureDefine theinformationarchitectureAssess and manage<strong>IT</strong> risksAssess and manage<strong>IT</strong> risksControlobjectivenumberPO2.1PO2.2Control objectiveEnterprise InformationArchitecture ModelEnterprise Data Dictionary andData Syntax RulesControl objective descriptionEstablish and maintain an enterprise information model to enable applicationsdevelopment and decision-supporting activities, consistent with <strong>IT</strong> plans asdescribed in PO1. The model should facilitate the optimal creation, use andsharing of information by the business in a way that maintains integrity and isflexible, functional, cost-effective, timely, secure and resilient to failure.Maintain an enterprise data dictionary that incorporates the organisation’sdata syntax rules. This dictionary should enable the sharing of data elementsamongst applications and systems, promote a common understanding of dataamongst <strong>IT</strong> and business users, and prevent incompatible data elements frombeing created.PO2.3 Data Classification Scheme Establish a classification scheme that applies throughout the enterprise, basedon the criticality and sensitivity (e.g., public, confidential, top secret) ofenterprise data. This scheme should include details about data ownership;definition of appropriate security levels and protection controls; and a briefdescription of data retention and destruction requirements, criticality andsensitivity. It should be used as the basis for applying controls such as accesscontrols, archiving or encryption.PO2.4 Integrity Management Define and implement procedures to ensure the integrity and consistency ofall data stored in electronic form, such as databases, data warehouses and dataarchives.PO9.1<strong>IT</strong> Risk ManagementFrameworkEstablish an <strong>IT</strong> risk management framework that is aligned to theorganisation’s (enterprise’s) risk management framework.PO9.2 Establishment of Risk Context Establish the context in which the risk assessment framework is applied toensure appropriate outcomes. This should include determining the internaland external context of each risk assessment, the goal of the assessment, andthe criteria against which risks are evaluated.----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Pagina 113