Risico’s van een gevirtualiseerde IT-omgeving
Risico's van een gevirtualiseerde IT-omgeving - Vurore
Risico's van een gevirtualiseerde IT-omgeving - Vurore
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
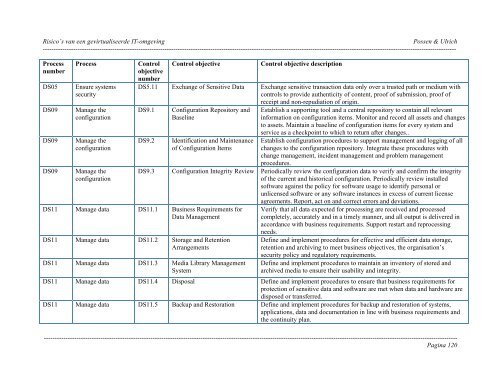
<strong>Risico’s</strong> <strong>van</strong> <strong>een</strong> <strong>gevirtualiseerde</strong> <strong>IT</strong>-<strong>omgeving</strong> Possen & Ulrich----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ProcessnumberDS05DS09DS09DS09ProcessEnsure systemssecurityManage theconfigurationManage theconfigurationManage theconfigurationControlobjectivenumberControl objectiveControl objective descriptionDS5.11 Exchange of Sensitive Data Exchange sensitive transaction data only over a trusted path or medium withcontrols to provide authenticity of content, proof of submission, proof ofDS9.1DS9.2Configuration Repository andBaselineIdentification and Maintenanceof Configuration Itemsreceipt and non-repudiation of origin.Establish a supporting tool and a central repository to contain all rele<strong>van</strong>tinformation on configuration items. Monitor and record all assets and changesto assets. Maintain a baseline of configuration items for every system andservice as a checkpoint to which to return after changes..Establish configuration procedures to support management and logging of allchanges to the configuration repository. Integrate these procedures withchange management, incident management and problem managementprocedures.DS9.3 Configuration Integrity Review Periodically review the configuration data to verify and confirm the integrityof the current and historical configuration. Periodically review installedsoftware against the policy for software usage to identify personal orunlicensed software or any software instances in excess of current licenseagreements. Report, act on and correct errors and deviations.DS11 Manage data DS11.1 Business Requirements forData ManagementDS11 Manage data DS11.2 Storage and RetentionArrangementsDS11 Manage data DS11.3 Media Library ManagementSystemVerify that all data expected for processing are received and processedcompletely, accurately and in a timely manner, and all output is delivered inaccordance with business requirements. Support restart and reprocessingneeds.Define and implement procedures for effective and efficient data storage,retention and archiving to meet business objectives, the organisation’ssecurity policy and regulatory requirements.Define and implement procedures to maintain an inventory of stored andarchived media to ensure their usability and integrity.DS11 Manage data DS11.4 Disposal Define and implement procedures to ensure that business requirements forprotection of sensitive data and software are met when data and hardware aredisposed or transferred.DS11 Manage data DS11.5 Backup and Restoration Define and implement procedures for backup and restoration of systems,applications, data and documentation in line with business requirements andthe continuity plan.----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Pagina 120