Risico’s van een gevirtualiseerde IT-omgeving
Risico's van een gevirtualiseerde IT-omgeving - Vurore
Risico's van een gevirtualiseerde IT-omgeving - Vurore
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
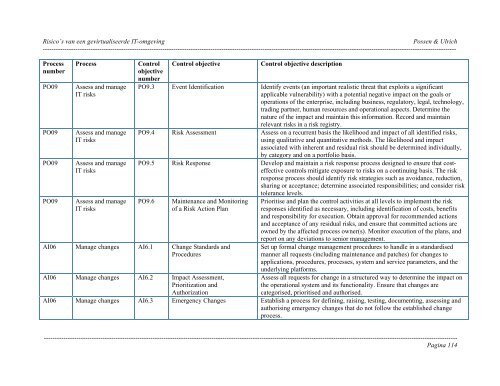
<strong>Risico’s</strong> <strong>van</strong> <strong>een</strong> <strong>gevirtualiseerde</strong> <strong>IT</strong>-<strong>omgeving</strong> Possen & Ulrich----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ProcessnumberPO09PO09PO09PO09ProcessAssess and manage<strong>IT</strong> risksAssess and manage<strong>IT</strong> risksAssess and manage<strong>IT</strong> risksAssess and manage<strong>IT</strong> risksControlobjectivenumberControl objectiveControl objective descriptionPO9.3 Event Identification Identify events (an important realistic threat that exploits a significantapplicable vulnerability) with a potential negative impact on the goals oroperations of the enterprise, including business, regulatory, legal, technology,trading partner, human resources and operational aspects. Determine thenature of the impact and maintain this information. Record and maintainrele<strong>van</strong>t risks in a risk registry.PO9.4 Risk Assessment Assess on a recurrent basis the likelihood and impact of all identified risks,using qualitative and quantitative methods. The likelihood and impactassociated with inherent and residual risk should be determined individually,by category and on a portfolio basis.PO9.5 Risk Response Develop and maintain a risk response process designed to ensure that costeffectivecontrols mitigate exposure to risks on a continuing basis. The riskresponse process should identify risk strategies such as avoidance, reduction,sharing or acceptance; determine associated responsibilities; and consider riskPO9.6Maintenance and Monitoringof a Risk Action PlanAI06 Manage changes AI6.1 Change Standards andProceduresAI06 Manage changes AI6.2 Impact Assessment,Prioritization andAuthorizationtolerance levels.Prioritise and plan the control activities at all levels to implement the riskresponses identified as necessary, including identification of costs, benefitsand responsibility for execution. Obtain approval for recommended actionsand acceptance of any residual risks, and ensure that committed actions areowned by the affected process owner(s). Monitor execution of the plans, andreport on any deviations to senior management.Set up formal change management procedures to handle in a standardisedmanner all requests (including maintenance and patches) for changes toapplications, procedures, processes, system and service parameters, and theunderlying platforms.Assess all requests for change in a structured way to determine the impact onthe operational system and its functionality. Ensure that changes arecategorised, prioritised and authorised.AI06 Manage changes AI6.3 Emergency Changes Establish a process for defining, raising, testing, documenting, assessing andauthorising emergency changes that do not follow the established changeprocess.----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Pagina 114