Risico’s van een gevirtualiseerde IT-omgeving
Risico's van een gevirtualiseerde IT-omgeving - Vurore
Risico's van een gevirtualiseerde IT-omgeving - Vurore
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
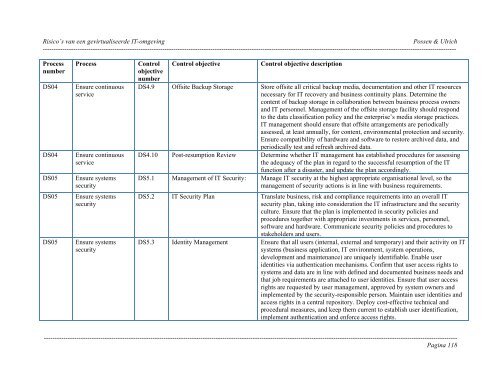
<strong>Risico’s</strong> <strong>van</strong> <strong>een</strong> <strong>gevirtualiseerde</strong> <strong>IT</strong>-<strong>omgeving</strong> Possen & Ulrich----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ProcessnumberDS04DS04DS05DS05DS05ProcessEnsure continuousserviceEnsure continuousserviceEnsure systemssecurityEnsure systemssecurityEnsure systemssecurityControlobjectivenumberControl objectiveControl objective descriptionDS4.9 Offsite Backup Storage Store offsite all critical backup media, documentation and other <strong>IT</strong> resourcesnecessary for <strong>IT</strong> recovery and business continuity plans. Determine thecontent of backup storage in collaboration betw<strong>een</strong> business process ownersand <strong>IT</strong> personnel. Management of the offsite storage facility should respondto the data classification policy and the enterprise’s media storage practices.<strong>IT</strong> management should ensure that offsite arrangements are periodicallyassessed, at least annually, for content, environmental protection and security.Ensure compatibility of hardware and software to restore archived data, andperiodically test and refresh archived data.DS4.10 Post-resumption Review Determine whether <strong>IT</strong> management has established procedures for assessingthe adequacy of the plan in regard to the successful resumption of the <strong>IT</strong>function after a disaster, and update the plan accordingly.DS5.1 Management of <strong>IT</strong> Security: Manage <strong>IT</strong> security at the highest appropriate organisational level, so themanagement of security actions is in line with business requirements.DS5.2 <strong>IT</strong> Security Plan Translate business, risk and compliance requirements into an overall <strong>IT</strong>security plan, taking into consideration the <strong>IT</strong> infrastructure and the securityculture. Ensure that the plan is implemented in security policies andprocedures together with appropriate investments in services, personnel,software and hardware. Communicate security policies and procedures tostakeholders and users.DS5.3 Identity Management Ensure that all users (internal, external and temporary) and their activity on <strong>IT</strong>systems (business application, <strong>IT</strong> environment, system operations,development and maintenance) are uniquely identifiable. Enable useridentities via authentication mechanisms. Confirm that user access rights tosystems and data are in line with defined and documented business needs andthat job requirements are attached to user identities. Ensure that user accessrights are requested by user management, approved by system owners andimplemented by the security-responsible person. Maintain user identities andaccess rights in a central repository. Deploy cost-effective technical andprocedural measures, and keep them current to establish user identification,implement authentication and enforce access rights.----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------Pagina 118