ENFORCEMENT
eop_ipec_jointstrategicplan_hi-res
eop_ipec_jointstrategicplan_hi-res
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
«<br />
Office of the Intellectual Property Enforcement Coordinator<br />
Dedicated IPR-infringing websites have widely<br />
promoted torrent VPNs, for example, to anonymize<br />
Internet protocol addresses and fake or hide a web user’s<br />
actual location when accessing libraries of infringing<br />
content in violation of applicable laws. 28 Platform<br />
operators who facilitate business models predicated<br />
on stolen content also develop their business models<br />
specifically to evade arrest or civil liability, increase<br />
enforcement costs, entice illicit traffic, and generate<br />
unreported income for the enterprise and its operators.<br />
For these and other reasons, law enforcement actions are<br />
often focused on the facilitating platform operator.<br />
These unlawful businesses generate income through<br />
a variety of payment methods, including: premium<br />
subscription fees and donations; payments in digital<br />
virtual currencies (such as Bitcoin, which commercialscale<br />
IP infringers often use to hide the proceeds<br />
of crime from the authorities); and revenue from<br />
advertisement and pay-per-click services. 29<br />
Operators of illicit sites deploy additional strategies<br />
to maximize income opportunities and safeguard<br />
revenue streams for those seeking to exploit unlicensed<br />
content on a commercial scale. For example, websites<br />
dedicated to profiting illegally from third-party content<br />
have been reported to generate hundreds of millions<br />
of dollars each year by exploiting payment processing<br />
and advertising network platforms in violation of law,<br />
and in material breach of the service provider’s and<br />
platform’s respective "Terms of Service." 30 A number<br />
of piracy sites are reported to use the stolen content<br />
(such as a hit movie) to lure consumers and then infect<br />
consumers’ computers with malware in order to conduct<br />
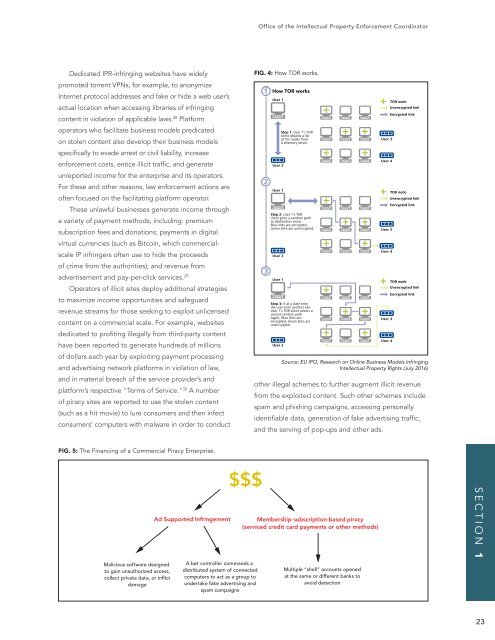
FIG. 4: How TOR works.<br />
Fig. 5: The Onion Router<br />
How TOR works<br />
User 1’s TOR<br />
User 1’s TOR<br />
unencrypted.<br />
User 1’s TOR client selects a<br />
unencrypted.<br />
part in its activities. It is also possible for the users to communicate with each other.<br />
other illegal schemes to further augment illicit revenue<br />
from the exploited content. Such other schemes include<br />
24 TRADEMARKS AND THE INTERNET, WIPO document SCT/24/4, 2010, and http://dictionary.reference.com/browse/virtual-environment<br />
spam and phishing campaigns, accessing personally<br />
18 · Research on Online Business Models Infringing Intellectual Property Rights<br />
identifiable data, generation of fake advertising traffic,<br />
and the serving of pop-ups and other ads.<br />
TOR node<br />
TOR node<br />
TOR node<br />
Virtual worlds<br />
Virtual worldsSource: 24 is most frequently EU IPO, used Research as a term that on describes Online the many Business different Models Infringing<br />
types of multiplayer online games and other multiuser Intellectual interactive worlds. Property Usually a Rights (July 2016)<br />
virtual world is 'populated' by avatars that are created by the individual users and<br />
who simultaneously and independently explore the virtual world and who takes<br />
«<br />
FIG. 5: The Financing of a Commercial Piracy Enterprise.<br />
Malicious software designed<br />
to gain unauthorized access,<br />
collect private data, or inflict<br />
damage<br />
Ad Supported Infringement<br />
$$$<br />
A bet controller commands a<br />
distributed system of connected<br />
computers to act as a group to<br />
undertake fake advertising and<br />
spam campaigns<br />
Membership subscription-based piracy<br />
(serviced credit card payments or other methods)<br />
Multiple “shell” accounts opened<br />
at the same or different banks to<br />
avoid detection<br />
SECTION 1<br />
23