ENFORCEMENT
eop_ipec_jointstrategicplan_hi-res
eop_ipec_jointstrategicplan_hi-res
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Joint Strategic Plan on Intellectual Property Enforcement<br />
One recent study, for example, probed a sample of<br />
800 websites dedicated to distributing pirated movies<br />
and television shows, and found that one out of every<br />
three content theft sites contained malware, including<br />
delivering adware 31 and botnets. 32 The study found that<br />
consumers are 28 times more likely to get malware from<br />
a content theft site than from similarly visited licensed<br />
content providers. 33 As such, it has been suggested<br />
the unscrupulous website operators exploit IP to “the<br />
detriment of society, businesses and the ordinary user of<br />
the Internet.” 34<br />
Canada, Hong Kong, Romania, and the United Arab<br />
Emirates. 35 Host locations changed every few minutes<br />
by use of an underground service that rotated the<br />
websites on computers that were part of a botnet<br />
of 450,000 “trojaned” systems, making a single<br />
website appear to be hosted in the United States at<br />
one moment, only to then appear to be hosted in<br />
Singapore at the next moment. 36<br />
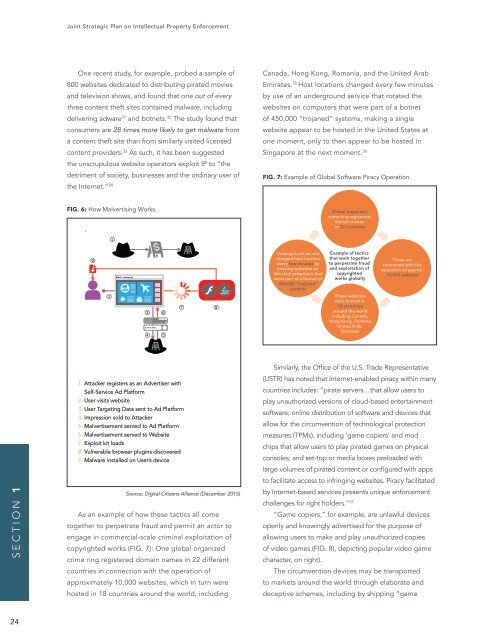
FIG. 7: Example of Global Software Piracy Operation.<br />
FIG. 6: How Malvertising Works.<br />
Global organized<br />
crime ring registered<br />
domain names<br />
in 22 countries<br />
Underground service<br />
changed host location<br />
every few minutes by<br />
rotating websites on<br />
infected computers that<br />
were part of a botnet of<br />
450,000 “trojaned”<br />
systems<br />
Example of tactics<br />
that work together<br />
to perpetrate fraud<br />
and exploitation of<br />
copyrighted<br />
works globally<br />
These websites<br />
were hosted in<br />
18 countries<br />
around the world<br />
including Canada,<br />
Hong Kong, Romania<br />
United Arab<br />
Emirates<br />
These are<br />
connected with the<br />
operation of approx.<br />
10,000 websites<br />
SECTION 1<br />
1. Attacker registers as an Advertiser with<br />
Self-Service Ad Platform<br />
2. User visits website<br />
3. User Targeting Data sent to Ad Platform<br />
4. Impression sold to Attacker<br />
5. Malvertisement served to Ad Platform<br />
6. Malvertisement served to Website<br />
7. Exploit kit loads<br />
8. Vulnerable browser plugins discovered<br />
9. Malware installed on User’s device<br />
Source: Digital Citizens Alliance (December 2015)<br />
As an example of how these tactics all come<br />
together to perpetrate fraud and permit an actor to<br />
engage in commercial-scale criminal exploitation of<br />
copyrighted works (FIG. 7): One global organized<br />
crime ring registered domain names in 22 different<br />
countries in connection with the operation of<br />
approximately 10,000 websites, which in turn were<br />
hosted in 18 countries around the world, including<br />
Similarly, the Office of the U.S. Trade Representative<br />
(USTR) has noted that Internet-enabled piracy within many<br />
countries includes: “pirate servers…that allow users to<br />
play unauthorized versions of cloud-based entertainment<br />
software; online distribution of software and devices that<br />
allow for the circumvention of technological protection<br />
measures (TPMs), including ‘game copiers’ and mod<br />
chips that allow users to play pirated games on physical<br />
consoles; and set-top or media boxes preloaded with<br />
large volumes of pirated content or configured with apps<br />
to facilitate access to infringing websites. Piracy facilitated<br />
by Internet-based services presents unique enforcement<br />
challenges for right holders.” 37<br />
“Game copiers,” for example, are unlawful devices<br />
openly and knowingly advertised for the purpose of<br />
allowing users to make and play unauthorized copies<br />
of video games (FIG. 8), depicting popular video game<br />
character, on right).<br />
The circumvention devices may be transported<br />
to markets around the world through elaborate and<br />
deceptive schemes, including by shipping “game<br />
24