Master Thesis - Hochschule Bonn-Rhein-Sieg
Master Thesis - Hochschule Bonn-Rhein-Sieg
Master Thesis - Hochschule Bonn-Rhein-Sieg
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
4. Overall evading concept <strong>Master</strong> <strong>Thesis</strong> Björn Ostermann page 40 of 126<br />
data remains consistent between two program calls, which is necessary during the testing and<br />
evaluating process of the program.<br />
The loading of the background data from a file, which is stored on the computer alongside the<br />
program, is realized in the second subpart (button 5). This process is the standard procedure of loading<br />
the background data into the program. Thus this subpart is automatically activated once, alongside the<br />
thread’s activation. The user only needs to take action in acquiring new background data, if the<br />
workplace was changed.<br />
If a change in the workplace occurred, new background data has to be acquired to guaranty a safe<br />
operation of the robot. The newly acquired background data has to be stored to the respective file by<br />
use of the third subpart (button 6). In this case, the currently stored background data in the file is<br />
overwritten with the background data in the program’s variable.<br />
Since other threads may work on the background data simultaneously, which can cause problems, all<br />
file operations of the program are handled by the data exchange object that takes special measures to<br />
avoid those problems (see chapter 4.6).<br />
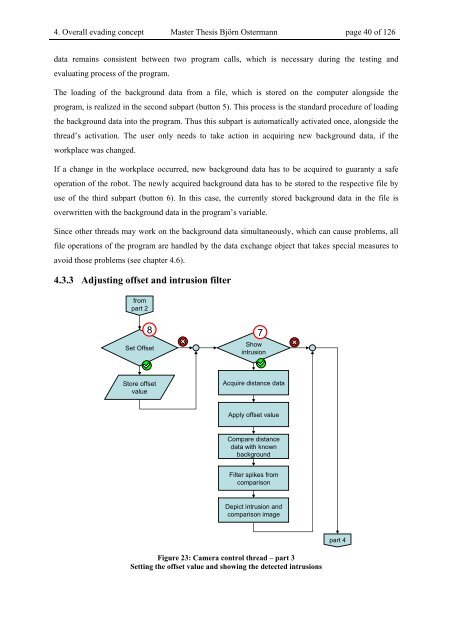
4.3.3 Adjusting offset and intrusion filter<br />
from<br />
part 2<br />
Set Offset<br />
Store offset<br />
value<br />
8 7<br />
Show<br />
intrusion<br />
Acquire distance data<br />
Apply offset value<br />
Compare distance<br />
data with known<br />
background<br />
Filter spikes from<br />
comparison<br />
Depict intrusion and<br />
comparison image<br />
Figure 23: Camera control thread – part 3<br />
Setting the offset value and showing the detected intrusions<br />
part 4