Norsk Telefoningeniørmøte 1992 - Telenor
Norsk Telefoningeniørmøte 1992 - Telenor
Norsk Telefoningeniørmøte 1992 - Telenor
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
4.2 Security Management<br />
Functions<br />
Security mechanisms management<br />
functions as discussed in chapter 3 shall<br />
include mainly:<br />
Key Management for generation, distribution<br />
and updating of RSA keys; initiation<br />
of periodical updates of DES key<br />
for IMSI-Ki database encryption, including<br />
its re-encryption.<br />
Authentication Management for operator<br />
access to highly security-sensitive nodes<br />
should be based on smart cards, with<br />
one-way authentication. Authentication<br />
parameters provided by the SMC.<br />
Authorisation and Access Control<br />
Management of operators provided<br />
locally with security event records on<br />
any change; remote barring of operators.<br />
Security Reporting and Auditing security<br />
alarms on events where security<br />
functions are affected like manual access<br />
to security box; security records on<br />
normal and abnormal security events of<br />
minor importance, collected in the nodes<br />
and transferred in a file to SMC on its<br />
request.<br />
4.3 Secure Communication<br />
Functionality<br />
GSM relies on the OSI framework for<br />
network management which is a prerequisite<br />
for a flexible and open<br />
architecture, allowing the interworking of<br />
network entities from different manufacturers.<br />
It provides also the freedom for<br />
supplementary additions (12.00).<br />
Additions in the application layer will be<br />
necessary until ongoing OSI standards<br />
for secure network management have<br />
been developed.<br />
Security management as part of systems<br />
management shall provide services and<br />
protocols for security-related management<br />
information transfer. This should be<br />
supported by enhancements to the ISO<br />
protocol stack. It is proposed to introduce<br />
specific Security Management Application<br />
Service Elements which shall provide<br />
services using the above mentioned<br />
security mechanisms. The security-ASE<br />
is still only a working document in ISO<br />
and it will probably not reach IS-status<br />
before 1994-95. For the time being it<br />
may be necessary to add security services<br />
in a sub-layer to the applications. It shall<br />
itself use the Common Management<br />
Information Service Element (CMISE)<br />
(12), ACSE (11) and ROSE (16).<br />
The following security services are<br />
recognised and will be used by the secure<br />
TMN functions:<br />
Secure Management Information Services,<br />
providing:<br />
- Authenticated Association Establishment<br />
and Authenticated Release,<br />
authentication parameters sent as user<br />
information<br />
- Secure Operation Service to interact by<br />
initiating actions with reply<br />
- Secure Notification Service for transfer<br />
of events with reply.<br />
The latter two services shall provide data<br />
integrity (signature over hashed data) and<br />
make use of the confirmed M-ACTION<br />
and M-EVENT services of CMISE in the<br />
confirmed mode.<br />
Secure File Transfer Service, providing:<br />
- File transfer with FTAM (10) enhanced<br />
with security mechanisms for<br />
data integrity and non-repudiation.<br />
This will require the use of ACSE and<br />
of M-ACTION for association establishments<br />
and for transfer of filename<br />
and control information.<br />
Secure communication functions make<br />
use of operations which deal with secret<br />
keys, e.g. for provision of signatures or<br />
data encryption. Such functions will be<br />
Functional<br />
"C" lib<br />
SCSI<br />
device<br />
driver<br />
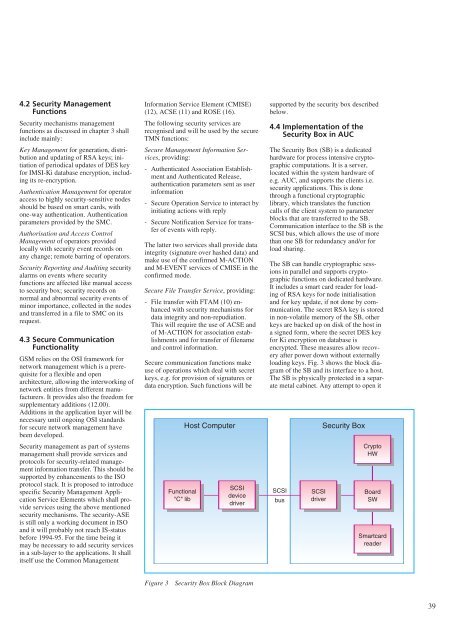
Figure 3 Security Box Block Diagram<br />
supported by the security box described<br />
below.<br />
4.4 Implementation of the<br />
Security Box in AUC<br />
The Security Box (SB) is a dedicated<br />
hardware for process intensive cryptographic<br />
computations. It is a server,<br />
located within the system hardware of<br />
e.g. AUC, and supports the clients i.e.<br />
security applications. This is done<br />
through a functional cryptographic<br />
library, which translates the function<br />
calls of the client system to parameter<br />
blocks that are transferred to the SB.<br />
Communication interface to the SB is the<br />
SCSI bus, which allows the use of more<br />
than one SB for redundancy and/or for<br />
load sharing.<br />
The SB can handle cryptographic sessions<br />
in parallel and supports cryptographic<br />
functions on dedicated hardware.<br />
It includes a smart card reader for loading<br />
of RSA keys for node initialisation<br />
and for key update, if not done by communication.<br />
The secret RSA key is stored<br />
in non-volatile memory of the SB, other<br />
keys are backed up on disk of the host in<br />
a signed form, where the secret DES key<br />
for Ki encryption on database is<br />
encrypted. These measures allow recovery<br />
after power down without externally<br />
loading keys. Fig. 3 shows the block diagram<br />
of the SB and its interface to a host.<br />
The SB is physically protected in a separate<br />
metal cabinet. Any attempt to open it<br />
Host Computer Security Box<br />
SCSI<br />
bus<br />
SCSI<br />
driver<br />
Crypto<br />
HW<br />
Board<br />
SW<br />
Smartcard<br />
reader<br />
39