Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
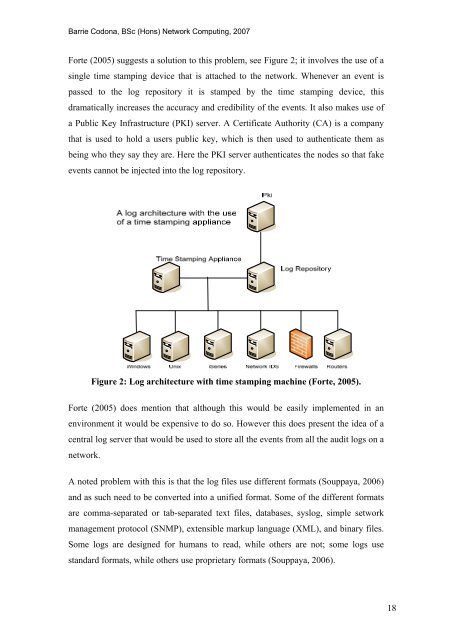
Forte (2005) suggests a solution to this problem, see Figure 2; it involves <strong>the</strong> use <strong>of</strong> a<br />
single time stamping device that is attached to <strong>the</strong> network. Whenever an event is<br />
passed to <strong>the</strong> log repository it is stamped by <strong>the</strong> time stamping device, this<br />
dramatically increases <strong>the</strong> accuracy <strong>and</strong> credibility <strong>of</strong> <strong>the</strong> events. It also makes use <strong>of</strong><br />
a Public Key Infrastructure (PKI) server. A Certificate Authority (CA) is a company<br />
that is used to hold a users public key, which is <strong>the</strong>n used to au<strong>the</strong>nticate <strong>the</strong>m as<br />
being who <strong>the</strong>y say <strong>the</strong>y are. Here <strong>the</strong> PKI server au<strong>the</strong>nticates <strong>the</strong> nodes so that fake<br />
events cannot be injected into <strong>the</strong> log repository.<br />
Figure 2: <strong>Log</strong> architecture with time stamping machine (Forte, 2005).<br />
Forte (2005) does mention that although this would be easily implemented in an<br />
environment it would be expensive to do so. However this does present <strong>the</strong> idea <strong>of</strong> a<br />
central log server that would be used to store all <strong>the</strong> events from all <strong>the</strong> audit logs on a<br />
network.<br />
A noted problem with this is that <strong>the</strong> log files use different formats (Souppaya, 2006)<br />
<strong>and</strong> as such need to be converted into a unified format. Some <strong>of</strong> <strong>the</strong> different formats<br />
are comma-separated or tab-separated text files, databases, syslog, simple setwork<br />
management protocol (SNMP), extensible markup language (XML), <strong>and</strong> binary files.<br />
Some logs are designed for humans to read, while o<strong>the</strong>rs are not; some logs use<br />
st<strong>and</strong>ard formats, while o<strong>the</strong>rs use proprietary formats (Souppaya, 2006).<br />
18









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





