Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
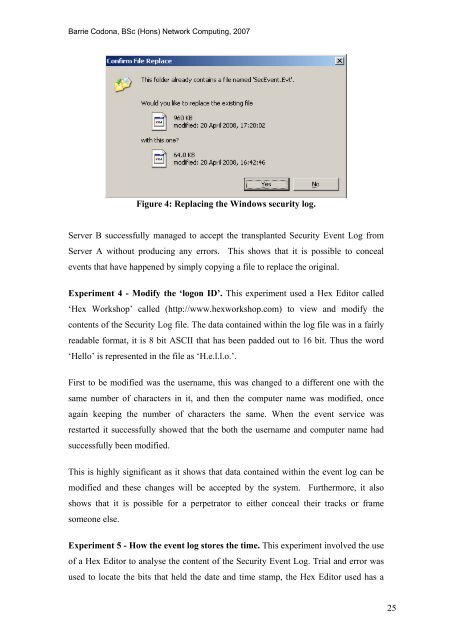
Figure 4: Replacing <strong>the</strong> <strong>Windows</strong> security log.<br />
Server B successfully managed to accept <strong>the</strong> transplanted Security <strong>Event</strong> <strong>Log</strong> from<br />
Server A without producing any errors. This shows that it is possible to conceal<br />
events that have happened by simply copying a file to replace <strong>the</strong> original.<br />
Experiment 4 - Modify <strong>the</strong> ‘logon ID’. This experiment used a Hex Editor called<br />
‘Hex Workshop’ called (http://www.hexworkshop.com) to view <strong>and</strong> modify <strong>the</strong><br />
contents <strong>of</strong> <strong>the</strong> Security <strong>Log</strong> file. The data contained within <strong>the</strong> log file was in a fairly<br />
readable format, it is 8 bit ASCII that has been padded out to 16 bit. Thus <strong>the</strong> word<br />
‘Hello’ is represented in <strong>the</strong> file as ‘H.e.l.l.o.’.<br />
First to be modified was <strong>the</strong> username, this was changed to a different one with <strong>the</strong><br />
same number <strong>of</strong> characters in it, <strong>and</strong> <strong>the</strong>n <strong>the</strong> computer name was modified, once<br />
again keeping <strong>the</strong> number <strong>of</strong> characters <strong>the</strong> same. When <strong>the</strong> event service was<br />
restarted it successfully showed that <strong>the</strong> both <strong>the</strong> username <strong>and</strong> computer name had<br />
successfully been modified.<br />
This is highly significant as it shows that data contained within <strong>the</strong> event log can be<br />
modified <strong>and</strong> <strong>the</strong>se changes will be accepted by <strong>the</strong> system. Fur<strong>the</strong>rmore, it also<br />
shows that it is possible for a perpetrator to ei<strong>the</strong>r conceal <strong>the</strong>ir tracks or frame<br />
someone else.<br />
Experiment 5 - How <strong>the</strong> event log stores <strong>the</strong> time. This experiment involved <strong>the</strong> use<br />
<strong>of</strong> a Hex Editor to analyse <strong>the</strong> content <strong>of</strong> <strong>the</strong> Security <strong>Event</strong> <strong>Log</strong>. Trial <strong>and</strong> error was<br />
used to locate <strong>the</strong> bits that held <strong>the</strong> date <strong>and</strong> time stamp, <strong>the</strong> Hex Editor used has a<br />
25









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





