Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
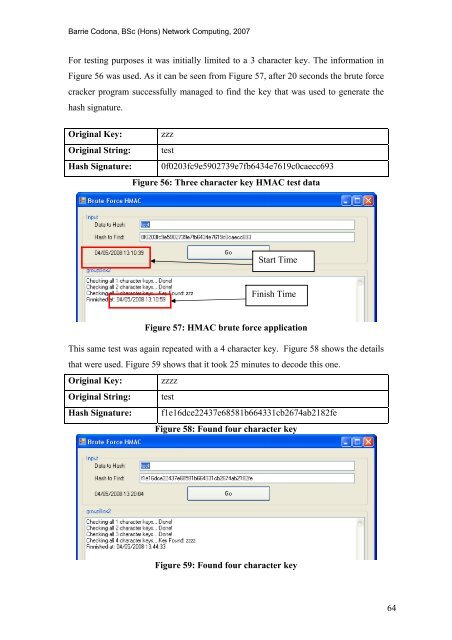
For testing purposes it was initially limited to a 3 character key. The information in<br />
Figure 56 was used. As it can be seen from Figure 57, after 20 seconds <strong>the</strong> brute force<br />
cracker program successfully managed to find <strong>the</strong> key that was used to generate <strong>the</strong><br />
hash signature.<br />
Original Key: zzz<br />
Original String: test<br />
Hash Signature: 0f0203fc9e5902739e7fb6434e7619c0caecc693<br />
Figure 56: Three character key HMAC test data<br />
Start Time<br />
Finish Time<br />
Figure 57: HMAC brute force application<br />
This same test was again repeated with a 4 character key. Figure 58 shows <strong>the</strong> details<br />
that were used. Figure 59 shows that it took 25 minutes to decode this one.<br />
Original Key: zzzz<br />
Original String: test<br />
Hash Signature: f1e16dce22437e68581b664331cb2674ab2182fe<br />
Figure 58: Found four character key<br />
Figure 59: Found four character key<br />
64









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





