Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
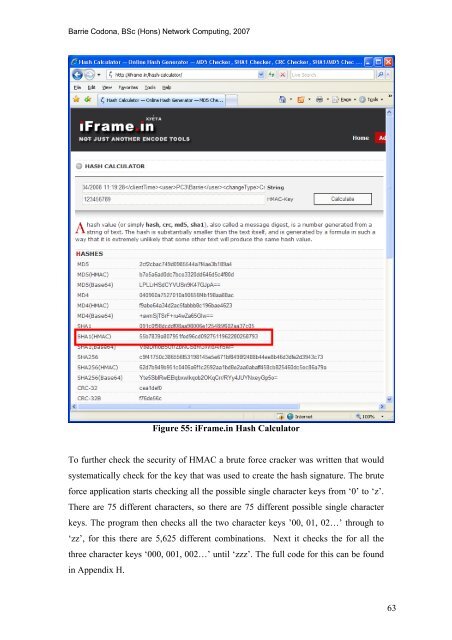
Figure 55: iFrame.in Hash Calculator<br />
To fur<strong>the</strong>r check <strong>the</strong> security <strong>of</strong> HMAC a brute force cracker was written that would<br />
systematically check for <strong>the</strong> key that was used to create <strong>the</strong> hash signature. The brute<br />
force application starts checking all <strong>the</strong> possible single character keys from ‘0’ to ‘z’.<br />
There are 75 different characters, so <strong>the</strong>re are 75 different possible single character<br />
keys. The program <strong>the</strong>n checks all <strong>the</strong> two character keys ’00, 01, 02…’ through to<br />
‘zz’, for this <strong>the</strong>re are 5,625 different combinations. Next it checks <strong>the</strong> for all <strong>the</strong><br />
three character keys ‘000, 001, 002…’ until ‘zzz’. The full code for this can be found<br />
in Appendix H.<br />
63









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





