Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
6.5 Experiment 2: Accuracy<br />
This experiment will be used to check <strong>the</strong> accuracy <strong>of</strong> <strong>the</strong> application, to ensure that<br />
all <strong>the</strong> events that are being generated are actually being captured by <strong>the</strong> application.<br />
The tester application was slightly modified to allow for an event log file to be<br />
modified, it now r<strong>and</strong>omly modifies <strong>the</strong> ‘Sec<strong>Event</strong>.txt’ file. For <strong>the</strong> purpose <strong>of</strong> this<br />
experiment a text file that is contained within a different directory to <strong>the</strong> data files,<br />
that are being created, is used to represent <strong>the</strong> event log file. The directory structure is<br />
represented by Figure 47.<br />
Data Files<br />
<strong>Event</strong> <strong>Log</strong> Files<br />
Figure 47: Test directory structure<br />
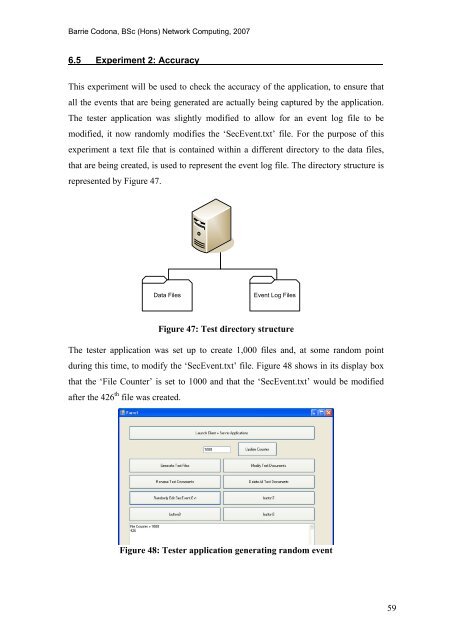
The tester application was set up to create 1,000 files <strong>and</strong>, at some r<strong>and</strong>om point<br />
during this time, to modify <strong>the</strong> ‘Sec<strong>Event</strong>.txt’ file. Figure 48 shows in its display box<br />
that <strong>the</strong> ‘File Counter’ is set to 1000 <strong>and</strong> that <strong>the</strong> ‘Sec<strong>Event</strong>.txt’ would be modified<br />
after <strong>the</strong> 426 th file was created.<br />
Figure 48: Tester application generating r<strong>and</strong>om event<br />
59









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





