Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
Both will have to be able to pass a number <strong>of</strong> pieces <strong>of</strong> information between each<br />
o<strong>the</strong>r.<br />
1. The Server is listening for a connection.<br />
2. The Client connects to <strong>the</strong> Server.<br />
3. The Server generates a r<strong>and</strong>om RSA key pair.<br />
4. The Server sends its public key to <strong>the</strong> Client.<br />
5. The Client receives <strong>the</strong> Servers public key <strong>and</strong> stores it in memory.<br />
6. The Client sends events to <strong>the</strong> server.<br />
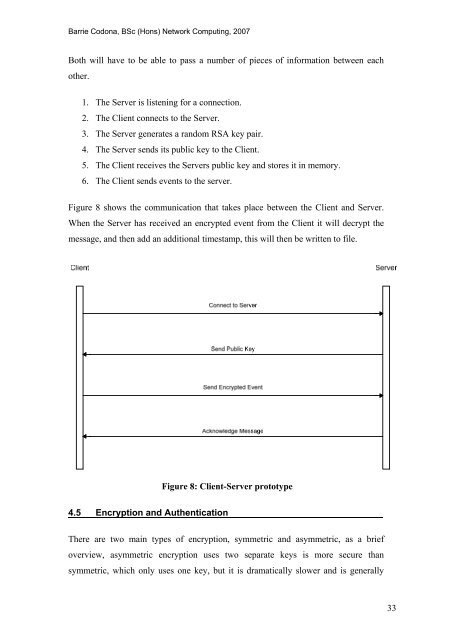
Figure 8 shows <strong>the</strong> communication that takes place between <strong>the</strong> Client <strong>and</strong> Server.<br />
When <strong>the</strong> Server has received an encrypted event from <strong>the</strong> Client it will decrypt <strong>the</strong><br />
message, <strong>and</strong> <strong>the</strong>n add an additional timestamp, this will <strong>the</strong>n be written to file.<br />
Figure 8: Client-Server prototype<br />
4.5 Encryption <strong>and</strong> Au<strong>the</strong>ntication<br />
There are two main types <strong>of</strong> encryption, symmetric <strong>and</strong> asymmetric, as a brief<br />
overview, asymmetric encryption uses two separate keys is more secure than<br />
symmetric, which only uses one key, but it is dramatically slower <strong>and</strong> is generally<br />
33









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





