Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
(Micros<strong>of</strong>t, 2008). This caused <strong>the</strong> FileSystemWatcher to crash <strong>and</strong> it <strong>the</strong>n failed to<br />
capture any o<strong>the</strong>r events, until <strong>the</strong> application was restarted.<br />
It had been suspected that <strong>the</strong> buffer overflow problem may have been caused by<br />
ei<strong>the</strong>r <strong>the</strong> size <strong>of</strong> <strong>the</strong> buffer, <strong>the</strong> HMAC tagging or <strong>the</strong> asymmetric encryption that was<br />
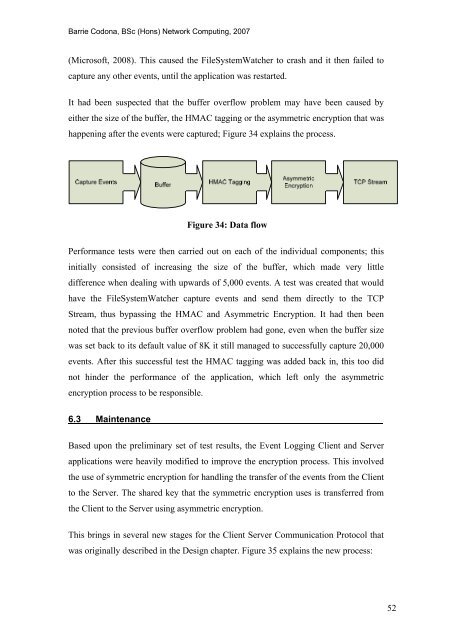
happening after <strong>the</strong> events were captured; Figure 34 explains <strong>the</strong> process.<br />
Figure 34: Data flow<br />
Performance tests were <strong>the</strong>n carried out on each <strong>of</strong> <strong>the</strong> individual components; this<br />
initially consisted <strong>of</strong> increasing <strong>the</strong> size <strong>of</strong> <strong>the</strong> buffer, which made very little<br />
difference when dealing with upwards <strong>of</strong> 5,000 events. A test was created that would<br />
have <strong>the</strong> FileSystemWatcher capture events <strong>and</strong> send <strong>the</strong>m directly to <strong>the</strong> TCP<br />
Stream, thus bypassing <strong>the</strong> HMAC <strong>and</strong> Asymmetric Encryption. It had <strong>the</strong>n been<br />
noted that <strong>the</strong> previous buffer overflow problem had gone, even when <strong>the</strong> buffer size<br />
was set back to its default value <strong>of</strong> 8K it still managed to successfully capture 20,000<br />
events. After this successful test <strong>the</strong> HMAC tagging was added back in, this too did<br />
not hinder <strong>the</strong> performance <strong>of</strong> <strong>the</strong> application, which left only <strong>the</strong> asymmetric<br />
encryption process to be responsible.<br />
6.3 Maintenance<br />
Based upon <strong>the</strong> preliminary set <strong>of</strong> test results, <strong>the</strong> <strong>Event</strong> <strong>Log</strong>ging Client <strong>and</strong> Server<br />
applications were heavily modified to improve <strong>the</strong> encryption process. This involved<br />
<strong>the</strong> use <strong>of</strong> symmetric encryption for h<strong>and</strong>ling <strong>the</strong> transfer <strong>of</strong> <strong>the</strong> events from <strong>the</strong> Client<br />
to <strong>the</strong> Server. The shared key that <strong>the</strong> symmetric encryption uses is transferred from<br />
<strong>the</strong> Client to <strong>the</strong> Server using asymmetric encryption.<br />
This brings in several new stages for <strong>the</strong> Client Server Communication Protocol that<br />
was originally described in <strong>the</strong> Design chapter. Figure 35 explains <strong>the</strong> new process:<br />
52









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





