Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
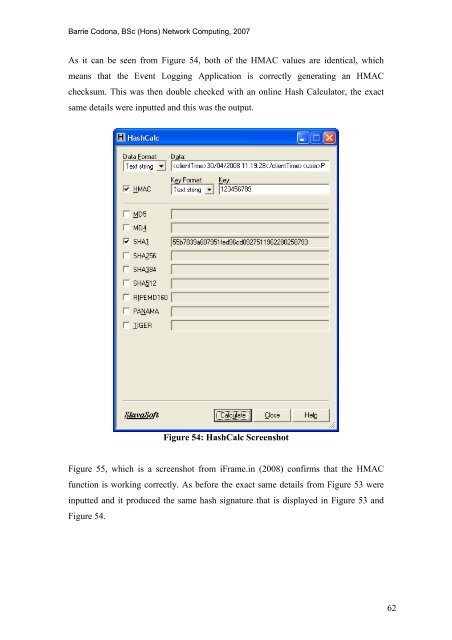
As it can be seen from Figure 54, both <strong>of</strong> <strong>the</strong> HMAC values are identical, which<br />
means that <strong>the</strong> <strong>Event</strong> <strong>Log</strong>ging Application is correctly generating an HMAC<br />
checksum. This was <strong>the</strong>n double checked with an online Hash Calculator, <strong>the</strong> exact<br />
same details were inputted <strong>and</strong> this was <strong>the</strong> output.<br />
Figure 54: HashCalc Screenshot<br />
Figure 55, which is a screenshot from iFrame.in (2008) confirms that <strong>the</strong> HMAC<br />
function is working correctly. As before <strong>the</strong> exact same details from Figure 53 were<br />
inputted <strong>and</strong> it produced <strong>the</strong> same hash signature that is displayed in Figure 53 <strong>and</strong><br />
Figure 54.<br />
62









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





