Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
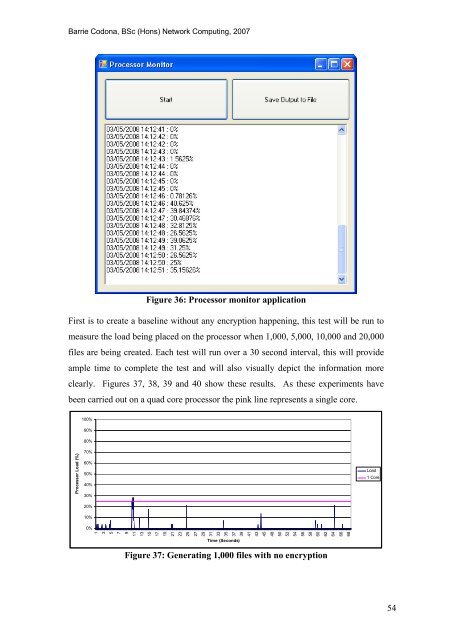
Figure 36: Processor monitor application<br />
First is to create a baseline without any encryption happening, this test will be run to<br />
measure <strong>the</strong> load being placed on <strong>the</strong> processor when 1,000, 5,000, 10,000 <strong>and</strong> 20,000<br />
files are being created. Each test will run over a 30 second interval, this will provide<br />
ample time to complete <strong>the</strong> test <strong>and</strong> will also visually depict <strong>the</strong> information more<br />
clearly. Figures 37, 38, 39 <strong>and</strong> 40 show <strong>the</strong>se results. As <strong>the</strong>se experiments have<br />
been carried out on a quad core processor <strong>the</strong> pink line represents a single core.<br />
100%<br />
90%<br />
80%<br />
Processor Load (%)<br />
70%<br />
60%<br />
50%<br />
40%<br />
30%<br />
20%<br />
10%<br />
0%<br />
Load<br />
1 Core<br />
1<br />
3<br />
5<br />
7<br />
9<br />
11<br />
13<br />
15<br />
17<br />
19<br />
21<br />
23<br />
25<br />
27<br />
29<br />
31<br />
33<br />
35<br />
37<br />
39<br />
41<br />
43<br />
45<br />
48<br />
50<br />
52<br />
54<br />
56<br />
58<br />
60<br />
62<br />
64<br />
66<br />
68<br />
Time (Seconds)<br />
Figure 37: Generating 1,000 files with no encryption<br />
54









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





