Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
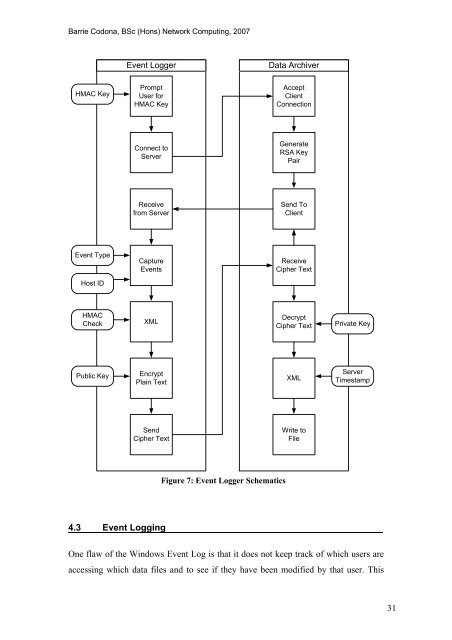
<strong>Event</strong> <strong>Log</strong>ger<br />
Data Archiver<br />
HMAC Key<br />
Prompt<br />
User for<br />
HMAC Key<br />
Accept<br />
Client<br />
Connection<br />
Connect to<br />
Server<br />
Generate<br />
RSA Key<br />
Pair<br />
Receive<br />
from Server<br />
Send To<br />
Client<br />
<strong>Event</strong> Type<br />
Capture<br />
<strong>Event</strong>s<br />
Receive<br />
Cipher Text<br />
Host ID<br />
HMAC<br />
Check<br />
XML<br />
Decrypt<br />
Cipher Text<br />
Private Key<br />
Public Key<br />
Encrypt<br />
Plain Text<br />
XML<br />
Server<br />
Timestamp<br />
Send<br />
Cipher Text<br />
Write to<br />
File<br />
Figure 7: <strong>Event</strong> <strong>Log</strong>ger Schematics<br />
4.3 <strong>Event</strong> <strong>Log</strong>ging<br />
One flaw <strong>of</strong> <strong>the</strong> <strong>Windows</strong> <strong>Event</strong> <strong>Log</strong> is that it does not keep track <strong>of</strong> which users are<br />
accessing which data files <strong>and</strong> to see if <strong>the</strong>y have been modified by that user. This<br />
31









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





