Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
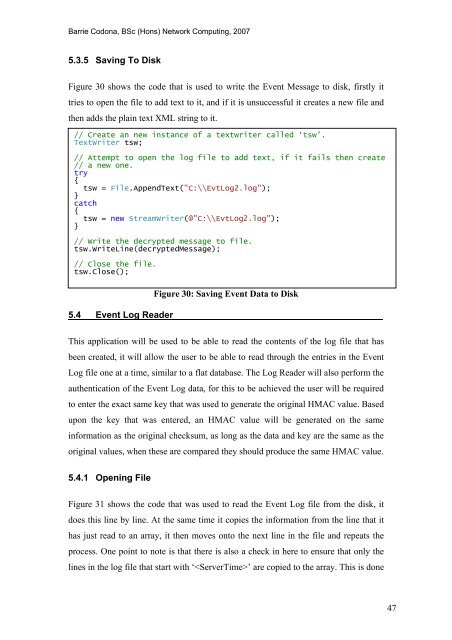
5.3.5 Saving To Disk<br />
Figure 30 shows <strong>the</strong> code that is used to write <strong>the</strong> <strong>Event</strong> Message to disk, firstly it<br />
tries to open <strong>the</strong> file to add text to it, <strong>and</strong> if it is unsuccessful it creates a new file <strong>and</strong><br />
<strong>the</strong>n adds <strong>the</strong> plain text XML string to it.<br />
// Create an new instance <strong>of</strong> a textwriter called ‘tsw’.<br />
TextWriter tsw;<br />
// Attempt to open <strong>the</strong> log file to add text, if it fails <strong>the</strong>n create<br />
// a new one.<br />
try<br />
{<br />
tsw = File.AppendText("C:\\Evt<strong>Log</strong>2.log");<br />
}<br />
catch<br />
{<br />
tsw = new StreamWriter(@"C:\\Evt<strong>Log</strong>2.log");<br />
}<br />
// Write <strong>the</strong> decrypted message to file.<br />
tsw.WriteLine(decryptedMessage);<br />
// Close <strong>the</strong> file.<br />
tsw.Close();<br />
5.4 <strong>Event</strong> <strong>Log</strong> Reader<br />
Figure 30: Saving <strong>Event</strong> Data to Disk<br />
This application will be used to be able to read <strong>the</strong> contents <strong>of</strong> <strong>the</strong> log file that has<br />
been created, it will allow <strong>the</strong> user to be able to read through <strong>the</strong> entries in <strong>the</strong> <strong>Event</strong><br />
<strong>Log</strong> file one at a time, similar to a flat database. The <strong>Log</strong> Reader will also perform <strong>the</strong><br />
au<strong>the</strong>ntication <strong>of</strong> <strong>the</strong> <strong>Event</strong> <strong>Log</strong> data, for this to be achieved <strong>the</strong> user will be required<br />
to enter <strong>the</strong> exact same key that was used to generate <strong>the</strong> original HMAC value. Based<br />
upon <strong>the</strong> key that was entered, an HMAC value will be generated on <strong>the</strong> same<br />
information as <strong>the</strong> original checksum, as long as <strong>the</strong> data <strong>and</strong> key are <strong>the</strong> same as <strong>the</strong><br />
original values, when <strong>the</strong>se are compared <strong>the</strong>y should produce <strong>the</strong> same HMAC value.<br />
5.4.1 Opening File<br />
Figure 31 shows <strong>the</strong> code that was used to read <strong>the</strong> <strong>Event</strong> <strong>Log</strong> file from <strong>the</strong> disk, it<br />
does this line by line. At <strong>the</strong> same time it copies <strong>the</strong> information from <strong>the</strong> line that it<br />
has just read to an array, it <strong>the</strong>n moves onto <strong>the</strong> next line in <strong>the</strong> file <strong>and</strong> repeats <strong>the</strong><br />
process. One point to note is that <strong>the</strong>re is also a check in here to ensure that only <strong>the</strong><br />
lines in <strong>the</strong> log file that start with ‘’ are copied to <strong>the</strong> array. This is done<br />
47









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





