Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
Analysis and Evaluation of the Windows Event Log - Bill Buchanan
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Barrie Codona, BSc (Hons) Network Computing, 2007<br />
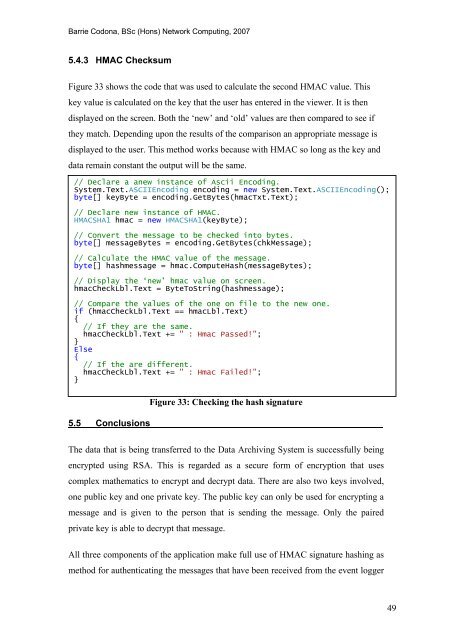
5.4.3 HMAC Checksum<br />
Figure 33 shows <strong>the</strong> code that was used to calculate <strong>the</strong> second HMAC value. This<br />
key value is calculated on <strong>the</strong> key that <strong>the</strong> user has entered in <strong>the</strong> viewer. It is <strong>the</strong>n<br />
displayed on <strong>the</strong> screen. Both <strong>the</strong> ‘new’ <strong>and</strong> ‘old’ values are <strong>the</strong>n compared to see if<br />
<strong>the</strong>y match. Depending upon <strong>the</strong> results <strong>of</strong> <strong>the</strong> comparison an appropriate message is<br />
displayed to <strong>the</strong> user. This method works because with HMAC so long as <strong>the</strong> key <strong>and</strong><br />
data remain constant <strong>the</strong> output will be <strong>the</strong> same.<br />
// Declare a anew instance <strong>of</strong> Ascii Encoding.<br />
System.Text.ASCIIEncoding encoding = new System.Text.ASCIIEncoding();<br />
byte[] keyByte = encoding.GetBytes(hmacTxt.Text);<br />
// Declare new instance <strong>of</strong> HMAC.<br />
HMACSHA1 hmac = new HMACSHA1(keyByte);<br />
// Convert <strong>the</strong> message to be checked into bytes.<br />
byte[] messageBytes = encoding.GetBytes(chkMessage);<br />
// Calculate <strong>the</strong> HMAC value <strong>of</strong> <strong>the</strong> message.<br />
byte[] hashmessage = hmac.ComputeHash(messageBytes);<br />
// Display <strong>the</strong> ‘new’ hmac value on screen.<br />
hmacCheckLbl.Text = ByteToString(hashmessage);<br />
// Compare <strong>the</strong> values <strong>of</strong> <strong>the</strong> one on file to <strong>the</strong> new one.<br />
if (hmacCheckLbl.Text == hmacLbl.Text)<br />
{<br />
// If <strong>the</strong>y are <strong>the</strong> same.<br />
hmacCheckLbl.Text += " : Hmac Passed!";<br />
}<br />
Else<br />
{<br />
// If <strong>the</strong> are different.<br />
hmacCheckLbl.Text += " : Hmac Failed!";<br />
}<br />
5.5 Conclusions<br />
Figure 33: Checking <strong>the</strong> hash signature<br />
The data that is being transferred to <strong>the</strong> Data Archiving System is successfully being<br />
encrypted using RSA. This is regarded as a secure form <strong>of</strong> encryption that uses<br />
complex ma<strong>the</strong>matics to encrypt <strong>and</strong> decrypt data. There are also two keys involved,<br />
one public key <strong>and</strong> one private key. The public key can only be used for encrypting a<br />
message <strong>and</strong> is given to <strong>the</strong> person that is sending <strong>the</strong> message. Only <strong>the</strong> paired<br />
private key is able to decrypt that message.<br />
All three components <strong>of</strong> <strong>the</strong> application make full use <strong>of</strong> HMAC signature hashing as<br />
method for au<strong>the</strong>nticating <strong>the</strong> messages that have been received from <strong>the</strong> event logger<br />
49









![Unit 5. Switches and VLANs [PDF]](https://img.yumpu.com/34422504/1/184x260/unit-5-switches-and-vlans-pdf.jpg?quality=85)





