4.0
1NSchAb
1NSchAb
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
106<br />
Web Application Penetration Testing<br />
1.2 GET<br />
• An example of a failed test (ie, the server supports OPTIONS despite<br />
no need for it):<br />
GET /index.html HTTP/1.1<br />
host: www.example.com<br />
1.3 HEAD<br />
HEAD /index.html HTTP/1.1<br />
host: www.example.com<br />
1.4 POST<br />
POST /index.html HTTP/1.1<br />
host: www.example.com<br />
#!/bin/bash<br />
for webservmethod in GET POST PUT TRACE CONNECT<br />
OPTIONS PROPFIND;<br />
do<br />
printf “$webservmethod “ ;<br />
printf “$webservmethod / HTTP/1.1\nHost: $1\n\n” | nc -q 1 $1<br />
80 | grep “HTTP/1.1”<br />
done<br />
1.5 PUT<br />
PUT /index.html HTTP/1.1<br />
host: www.example.com<br />
1.6 DELETE<br />
DELETE /index.html HTTP/1.1<br />
host: www.example.com<br />
1.7 TRACE<br />
TRACE /index.html HTTP/1.1<br />
host: www.example.com<br />
1.8 CONNECT<br />
CONNECT /index.html HTTP/1.1<br />
host: www.example.com<br />
2. Sending HTTP requests<br />
• For each method and/or method text file, send the request to<br />
nc www.example.com 80 < OPTIONS.http.txt<br />
your web server via netcat or telnet on port 80 (HTTP):<br />
3. Parsing HTTP responses<br />
• Although each HTTP method can potentially return different results,<br />
there is only a single valid result for all methods other than<br />
GET and POST.<br />
The web server should either ignore the request completely or return<br />
an error. Any other response indicates a test failure as the<br />
server is responding to methods/verbs that are unnecessary.<br />
These methods should be disabled.<br />
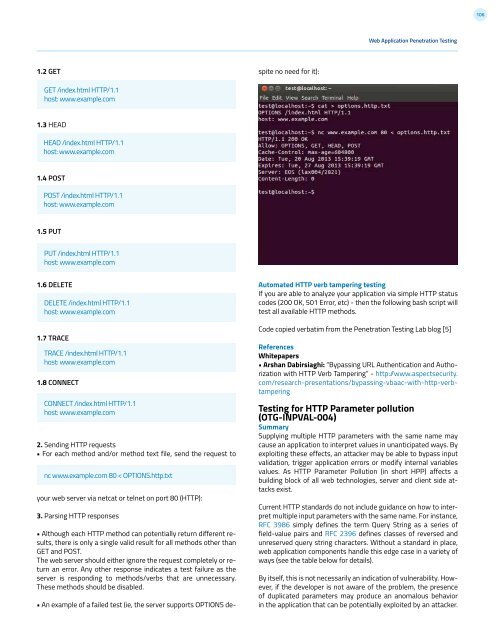
Automated HTTP verb tampering testing<br />
If you are able to analyze your application via simple HTTP status<br />
codes (200 OK, 501 Error, etc) - then the following bash script will<br />
test all available HTTP methods.<br />
Code copied verbatim from the Penetration Testing Lab blog [5]<br />
References<br />
Whitepapers<br />
• Arshan Dabirsiaghi: “Bypassing URL Authentication and Authorization<br />
with HTTP Verb Tampering” - http: /www.aspectsecurity.<br />
com/research-presentations/bypassing-vbaac-with-http-verbtampering<br />
Testing for HTTP Parameter pollution<br />
(OTG-INPVAL-004)<br />
Summary<br />
Supplying multiple HTTP parameters with the same name may<br />
cause an application to interpret values in unanticipated ways. By<br />
exploiting these effects, an attacker may be able to bypass input<br />
validation, trigger application errors or modify internal variables<br />
values. As HTTP Parameter Pollution (in short HPP) affects a<br />
building block of all web technologies, server and client side attacks<br />
exist.<br />
Current HTTP standards do not include guidance on how to interpret<br />
multiple input parameters with the same name. For instance,<br />
RFC 3986 simply defines the term Query String as a series of<br />
field-value pairs and RFC 2396 defines classes of reversed and<br />
unreserved query string characters. Without a standard in place,<br />
web application components handle this edge case in a variety of<br />
ways (see the table below for details).<br />
By itself, this is not necessarily an indication of vulnerability. However,<br />
if the developer is not aware of the problem, the presence<br />
of duplicated parameters may produce an anomalous behavior<br />
in the application that can be potentially exploited by an attacker.