4.0
1NSchAb
1NSchAb
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
205<br />
Web Application Penetration Testing<br />
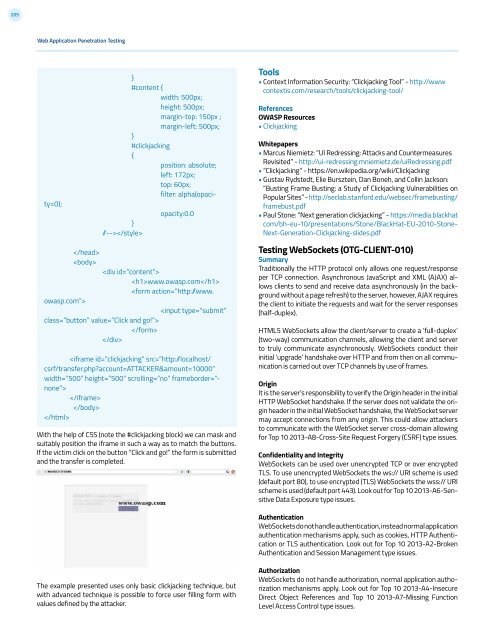
}<br />
#content {<br />
width: 500px;<br />
height: 500px;<br />
margin-top: 150px ;<br />
margin-left: 500px;<br />
}<br />
#clickjacking<br />
{<br />
position: absolute;<br />
left: 172px;<br />
top: 60px;<br />
filter: alpha(opacity=0);<br />
}<br />
/--><br />
opacity:0.0<br />
Tools<br />
• Context Information Security: “Clickjacking Tool” - http://www<br />
contextis.com/research/tools/clickjacking-tool/<br />
References<br />
OWASP Resources<br />
• Clickjacking<br />
Whitepapers<br />
• Marcus Niemietz: “UI Redressing: Attacks and Countermeasures<br />
Revisited” - http://ui-redressing.mniemietz.de/uiRedressing.pdf<br />
• “Clickjacking” - https://en.wikipedia.org/wiki/Clickjacking<br />
• Gustav Rydstedt, Elie Bursztein, Dan Boneh, and Collin Jackson:<br />
“Busting Frame Busting: a Study of Clickjacking Vulnerabilities on<br />
Popular Sites” - http://seclab.stanford.edu/websec/framebusting/<br />
framebust.pdf<br />
• Paul Stone: “Next generation clickjacking” - https://media.blackhat<br />
com/bh-eu-10/presentations/Stone/BlackHat-EU-2010-Stone-<br />
Next-Generation-Clickjacking-slides.pdf<br />
<br />
<br />
<br />
www.owasp.com<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
<br />
With the help of CSS (note the #clickjacking block) we can mask and<br />
suitably position the iframe in such a way as to match the buttons.<br />
If the victim click on the button “Click and go!” the form is submitted<br />
and the transfer is completed.<br />
Testing WebSockets (OTG-CLIENT-010)<br />
Summary<br />
Traditionally the HTTP protocol only allows one request/response<br />
per TCP connection. Asynchronous JavaScript and XML (AJAX) allows<br />
clients to send and receive data asynchronously (in the background<br />
without a page refresh) to the server, however, AJAX requires<br />
the client to initiate the requests and wait for the server responses<br />
(half-duplex).<br />
HTML5 WebSockets allow the client/server to create a ‘full-duplex’<br />
(two-way) communication channels, allowing the client and server<br />
to truly communicate asynchronously. WebSockets conduct their<br />
initial ‘upgrade’ handshake over HTTP and from then on all communication<br />
is carried out over TCP channels by use of frames.<br />
Origin<br />
It is the server’s responsibility to verify the Origin header in the initial<br />
HTTP WebSocket handshake. If the server does not validate the origin<br />
header in the initial WebSocket handshake, the WebSocket server<br />
may accept connections from any origin. This could allow attackers<br />
to communicate with the WebSocket server cross-domain allowing<br />
for Top 10 2013-A8-Cross-Site Request Forgery (CSRF) type issues.<br />
Confidentiality and Integrity<br />
WebSockets can be used over unencrypted TCP or over encrypted<br />
TLS. To use unencrypted WebSockets the ws:// URI scheme is used<br />
(default port 80), to use encrypted (TLS) WebSockets the wss:// URI<br />
scheme is used (default port 443). Look out for Top 10 2013-A6-Sensitive<br />
Data Exposure type issues.<br />
Authentication<br />
WebSockets do not handle authentication, instead normal application<br />
authentication mechanisms apply, such as cookies, HTTP Authentication<br />
or TLS authentication. Look out for Top 10 2013-A2-Broken<br />
Authentication and Session Management type issues.<br />
The example presented uses only basic clickjacking technique, but<br />
with advanced technique is possible to force user filling form with<br />
values defined by the attacker.<br />
Authorization<br />
WebSockets do not handle authorization, normal application authorization<br />
mechanisms apply. Look out for Top 10 2013-A4-Insecure<br />
Direct Object References and Top 10 2013-A7-Missing Function<br />
Level Access Control type issues.