4.0
1NSchAb
1NSchAb
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
147<br />
Web Application Penetration Testing<br />
overwriting the instruction pointer, similar results can also be<br />
obtained by overwriting other variables and structures, like Exception<br />
Handlers, which are located on the stack.<br />
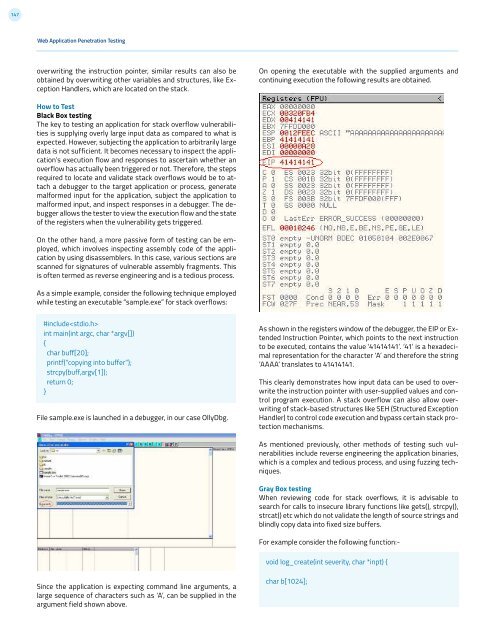
On opening the executable with the supplied arguments and<br />
continuing execution the following results are obtained.<br />
How to Test<br />
Black Box testing<br />
The key to testing an application for stack overflow vulnerabilities<br />
is supplying overly large input data as compared to what is<br />
expected. However, subjecting the application to arbitrarily large<br />
data is not sufficient. It becomes necessary to inspect the application’s<br />
execution flow and responses to ascertain whether an<br />
overflow has actually been triggered or not. Therefore, the steps<br />
required to locate and validate stack overflows would be to attach<br />
a debugger to the target application or process, generate<br />
malformed input for the application, subject the application to<br />
malformed input, and inspect responses in a debugger. The debugger<br />
allows the tester to view the execution flow and the state<br />
of the registers when the vulnerability gets triggered.<br />
On the other hand, a more passive form of testing can be employed,<br />
which involves inspecting assembly code of the application<br />
by using disassemblers. In this case, various sections are<br />
scanned for signatures of vulnerable assembly fragments. This<br />
is often termed as reverse engineering and is a tedious process.<br />
As a simple example, consider the following technique employed<br />
while testing an executable “sample.exe” for stack overflows:<br />
#include<br />
int main(int argc, char *argv[])<br />
{<br />
char buff[20];<br />
printf(“copying into buffer”);<br />
strcpy(buff,argv[1]);<br />
return 0;<br />
}<br />
File sample.exe is launched in a debugger, in our case OllyDbg.<br />
As shown in the registers window of the debugger, the EIP or Extended<br />
Instruction Pointer, which points to the next instruction<br />
to be executed, contains the value ‘41414141’. ‘41’ is a hexadecimal<br />
representation for the character ‘A’ and therefore the string<br />
‘AAAA’ translates to 41414141.<br />
This clearly demonstrates how input data can be used to overwrite<br />
the instruction pointer with user-supplied values and control<br />
program execution. A stack overflow can also allow overwriting<br />
of stack-based structures like SEH (Structured Exception<br />
Handler) to control code execution and bypass certain stack protection<br />
mechanisms.<br />
As mentioned previously, other methods of testing such vulnerabilities<br />
include reverse engineering the application binaries,<br />
which is a complex and tedious process, and using fuzzing techniques.<br />
Gray Box testing<br />
When reviewing code for stack overflows, it is advisable to<br />
search for calls to insecure library functions like gets(), strcpy(),<br />
strcat() etc which do not validate the length of source strings and<br />
blindly copy data into fixed size buffers.<br />
For example consider the following function:-<br />
void log_create(int severity, char *inpt) {<br />
Since the application is expecting command line arguments, a<br />
large sequence of characters such as ‘A’, can be supplied in the<br />
argument field shown above.<br />
char b[1024];