4.0
1NSchAb
1NSchAb
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
199<br />
Web Application Penetration Testing<br />
since the internal JavaScript which is executed by the browser<br />
will be something similar to:<br />
eval(‘try { __flash__toXML(‘+__root.callback+’) ; } catch (e) {<br />
“”; }’)<br />
HTML Injection<br />
TextField Objects can render minimal HTML by setting:<br />
tf.html = true<br />
tf.htmlText = ‘text’<br />
So if some part of text could be controlled by the tester, an A tag<br />
or an IMG tag could be injected resulting in modifying the GUI or<br />
XSS the browser.<br />
Some attack examples with A Tag:<br />
• Direct XSS: <br />
• Call a function: <br />
• Call SWF public functions:<br />
<br />
• Call native static as function:<br />
IMG tag could be used as well:<br />
<br />
(.swf is necessary to<br />
bypass flash player internal filter)<br />
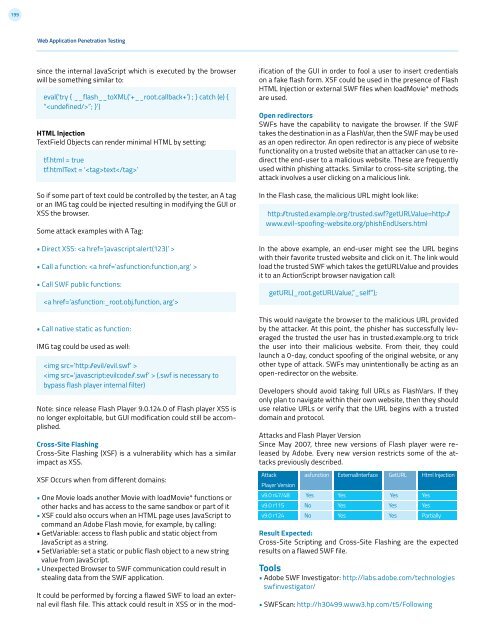
Note: since release Flash Player 9.0.12<strong>4.0</strong> of Flash player XSS is<br />
no longer exploitable, but GUI modification could still be accomplished.<br />
Cross-Site Flashing<br />
Cross-Site Flashing (XSF) is a vulnerability which has a similar<br />
impact as XSS.<br />
XSF Occurs when from different domains:<br />
• One Movie loads another Movie with loadMovie* functions or<br />
other hacks and has access to the same sandbox or part of it<br />
• XSF could also occurs when an HTML page uses JavaScript to<br />
command an Adobe Flash movie, for example, by calling:<br />
• GetVariable: access to flash public and static object from<br />
JavaScript as a string.<br />
• SetVariable: set a static or public flash object to a new string<br />
value from JavaScript.<br />
• Unexpected Browser to SWF communication could result in<br />
stealing data from the SWF application.<br />
It could be performed by forcing a flawed SWF to load an external<br />
evil flash file. This attack could result in XSS or in the modification<br />
of the GUI in order to fool a user to insert credentials<br />
on a fake flash form. XSF could be used in the presence of Flash<br />
HTML Injection or external SWF files when loadMovie* methods<br />
are used.<br />
Open redirectors<br />
SWFs have the capability to navigate the browser. If the SWF<br />
takes the destination in as a FlashVar, then the SWF may be used<br />
as an open redirector. An open redirector is any piece of website<br />
functionality on a trusted website that an attacker can use to redirect<br />
the end-user to a malicious website. These are frequently<br />
used within phishing attacks. Similar to cross-site scripting, the<br />
attack involves a user clicking on a malicious link.<br />
In the Flash case, the malicious URL might look like:<br />
http: /trusted.example.org/trusted.swf?getURLValue=http: /<br />
www.evil-spoofing-website.org/phishEndUsers.html<br />
In the above example, an end-user might see the URL begins<br />
with their favorite trusted website and click on it. The link would<br />
load the trusted SWF which takes the getURLValue and provides<br />
it to an ActionScript browser navigation call:<br />
getURL(_root.getURLValue,”_self”);<br />
This would navigate the browser to the malicious URL provided<br />
by the attacker. At this point, the phisher has successfully leveraged<br />
the trusted the user has in trusted.example.org to trick<br />
the user into their malicious website. From their, they could<br />
launch a 0-day, conduct spoofing of the original website, or any<br />
other type of attack. SWFs may unintentionally be acting as an<br />
open-redirector on the website.<br />
Developers should avoid taking full URLs as FlashVars. If they<br />
only plan to navigate within their own website, then they should<br />
use relative URLs or verify that the URL begins with a trusted<br />
domain and protocol.<br />
Attacks and Flash Player Version<br />
Since May 2007, three new versions of Flash player were released<br />
by Adobe. Every new version restricts some of the attacks<br />
previously described.<br />
Attack<br />
Player Version<br />
v9.0 r47/48<br />
v9.0 r115<br />
v9.0 r124<br />
asfunction<br />
Yes<br />
No<br />
No<br />
ExternalInterface<br />
Yes<br />
Yes<br />
Yes<br />
GetURL<br />
Yes<br />
Yes<br />
Yes<br />
Result Expected:<br />
Cross-Site Scripting and Cross-Site Flashing are the expected<br />
results on a flawed SWF file.<br />
Tools<br />
• Adobe SWF Investigator: http://labs.adobe.com/technologies<br />
swfinvestigator/<br />
• SWFScan: http://h30499.www3.hp.com/t5/Following<br />
Html Injection<br />
Yes<br />
Yes<br />
Partially