Proceedings 2002/2003 - IRSE
Proceedings 2002/2003 - IRSE
Proceedings 2002/2003 - IRSE
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
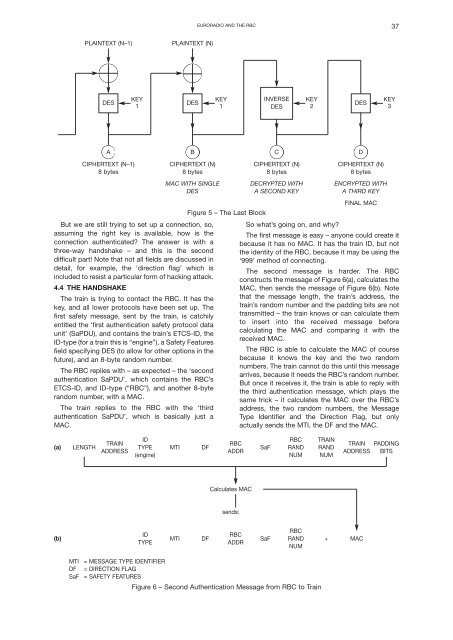
EURORADIO AND THE RBC 37<br />
PLAINTEXT (N–1)<br />
PLAINTEXT (N)<br />
DES<br />
KEY<br />
1<br />
DES<br />
KEY<br />
1<br />
INVERSE<br />
DES<br />
KEY<br />
2<br />
DES<br />
KEY<br />
3<br />
A<br />
B<br />
C<br />
D<br />
CIPHERTEXT (N–1)<br />
8 bytes<br />
CIPHERTEXT (N)<br />
8 bytes<br />
MAC WITH SINGLE<br />
DES<br />
But we are still trying to set up a connection, so,<br />
assuming the right key is available, how is the<br />
connection authenticated? The answer is with a<br />
three-way handshake – and this is the second<br />
difficult part! Note that not all fields are discussed in<br />
detail, for example, the ‘direction flag’ which is<br />
included to resist a particular form of hacking attack.<br />
4.4 THE HANDSHAKE<br />
The train is trying to contact the RBC. It has the<br />
key, and all lower protocols have been set up. The<br />
first safety message, sent by the train, is catchily<br />
entitled the ‘first authentication safety protocol data<br />
unit’ (SaPDU), and contains the train’s ETCS-ID, the<br />
ID-type (for a train this is “engine”), a Safety Features<br />
field specifying DES (to allow for other options in the<br />
future), and an 8-byte random number.<br />
The RBC replies with – as expected – the ‘second<br />
authentication SaPDU’, which contains the RBC’s<br />
ETCS-ID, and ID-type (“RBC”), and another 8-byte<br />
random number, with a MAC.<br />
The train replies to the RBC with the ‘third<br />
authentication SaPDU’, which is basically just a<br />
MAC.<br />
Figure 5 – The Last Block<br />
CIPHERTEXT (N)<br />
8 bytes<br />
DECRYPTED WITH<br />
A SECOND KEY<br />
CIPHERTEXT (N)<br />
8 bytes<br />
ENCRYPTED WITH<br />
A THIRD KEY<br />
FINAL MAC<br />
So what’s going on, and why?<br />
The first message is easy – anyone could create it<br />
because it has no MAC. It has the train ID, but not<br />
the identity of the RBC, because it may be using the<br />
‘999’ method of connecting.<br />
The second message is harder. The RBC<br />
constructs the message of Figure 6(a), calculates the<br />
MAC, then sends the message of Figure 6(b). Note<br />
that the message length, the train’s address, the<br />
train’s random number and the padding bits are not<br />
transmitted – the train knows or can calculate them<br />
to insert into the received message before<br />
calculating the MAC and comparing it with the<br />
received MAC.<br />
The RBC is able to calculate the MAC of course<br />
because it knows the key and the two random<br />
numbers. The train cannot do this until this message<br />
arrives, because it needs the RBC’s random number.<br />
But once it receives it, the train is able to reply with<br />
the third authentication message, which plays the<br />
same trick – it calculates the MAC over the RBC’s<br />
address, the two random numbers, the Message<br />
Type Identifier and the Direction Flag, but only<br />
actually sends the MTI, the DF and the MAC.<br />
(a)<br />
LENGTH<br />
ID RBC TRAIN<br />
TRAIN<br />
RBC<br />
TYPE MTI DF<br />
SaF RAND RAND<br />
ADDRESS ADDR<br />
(engine) NUM NUM<br />
TRAIN<br />
ADDRESS<br />
PADDING<br />
BITS<br />
Calculates MAC<br />
sends:<br />
(b)<br />
ID<br />
TYPE<br />
MTI<br />
DF<br />
RBC<br />
ADDR<br />
RBC<br />
SaF RAND + MAC<br />
NUM<br />
MTI<br />
DF<br />
SaF<br />
= MESSAGE TYPE IDENTIFIER<br />
= DIRECTION FLAG<br />
= SAFETY FEATURES<br />
Figure 6 – Second Authentication Message from RBC to Train