COP_2023_V7_pages
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
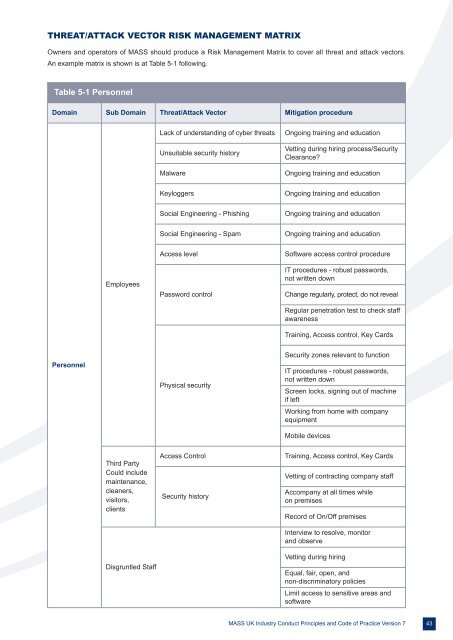
THREAT/ATTACK VECTOR RISK MANAGEMENT MATRIX<br />
Owners and operators of MASS should produce a Risk Management Matrix to cover all threat and attack vectors.<br />
An example matrix is shown is at Table 5-1 following.<br />
Table 5-1 Personnel<br />
Domain Sub Domain Threat/Attack Vector Mitigation procedure<br />
Lack of understanding of cyber threats<br />
Unsuitable security history<br />
Malware<br />
Ongoing training and education<br />
Vetting during hiring process/Security<br />
Clearance?<br />
Ongoing training and education<br />
Keyloggers<br />
Ongoing training and education<br />
Social Engineering - Phishing<br />
Ongoing training and education<br />
Social Engineering - Spam<br />
Ongoing training and education<br />
Employees<br />
Access level<br />
Password control<br />
Software access control procedure<br />
IT procedures - robust passwords,<br />
not written down<br />
Change regularly, protect, do not reveal<br />
Regular penetration test to check staff<br />
awareness<br />
Training, Access control, Key Cards<br />
Personnel<br />
Physical security<br />
Security zones relevant to function<br />
IT procedures - robust passwords,<br />
not written down<br />
Screen locks, signing out of machine<br />
if left<br />
Working from home with company<br />
equipment<br />
Mobile devices<br />
Third Party<br />
Could include<br />
maintenance,<br />
cleaners,<br />
visitors,<br />
clients<br />
Disgruntled Staff<br />
Access Control<br />
Security history<br />
Training, Access control, Key Cards<br />
Vetting of contracting company staff<br />
Accompany at all times while<br />
on premises<br />
Record of On/Off premises<br />
Interview to resolve, monitor<br />
and observe<br />
Vetting during hiring<br />
Equal, fair, open, and<br />
non-discriminatory policies<br />
Limit access to sensitive areas and<br />
software<br />
MASS UK Industry Conduct Principles and Code of Practice Version 7<br />
43