CCNA Complete Guide 2nd Edition.pdf - Cisco Learning Home
CCNA Complete Guide 2nd Edition.pdf - Cisco Learning Home
CCNA Complete Guide 2nd Edition.pdf - Cisco Learning Home
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
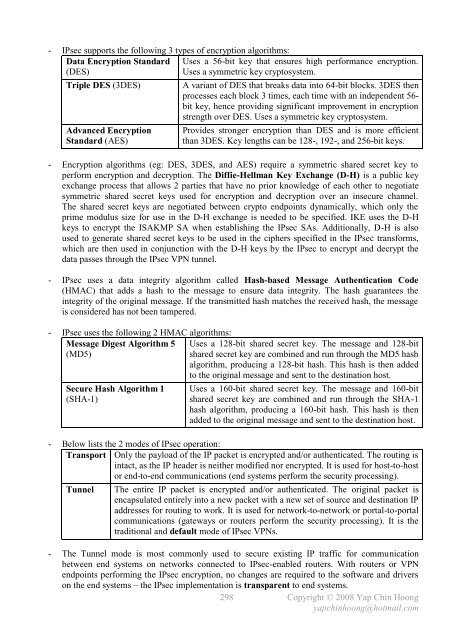
- IPsec supports the following 3 types of encryption algorithms:<br />
Data Encryption Standard<br />
(DES)<br />
Uses a 56-bit key that ensures high performance encryption.<br />
Uses a symmetric key cryptosystem.<br />
Triple DES (3DES) A variant of DES that breaks data into 64-bit blocks. 3DES then<br />
processes each block 3 times, each time with an independent 56bit<br />
key, hence providing significant improvement in encryption<br />
strength over DES. Uses a symmetric key cryptosystem.<br />
Advanced Encryption<br />
Standard (AES)<br />
Provides stronger encryption than DES and is more efficient<br />
than 3DES. Key lengths can be 128-, 192-, and 256-bit keys.<br />
- Encryption algorithms (eg: DES, 3DES, and AES) require a symmetric shared secret key to<br />
perform encryption and decryption. The Diffie-Hellman Key Exchange (D-H) is a public key<br />
exchange process that allows 2 parties that have no prior knowledge of each other to negotiate<br />
symmetric shared secret keys used for encryption and decryption over an insecure channel.<br />
The shared secret keys are negotiated between crypto endpoints dynamically, which only the<br />
prime modulus size for use in the D-H exchange is needed to be specified. IKE uses the D-H<br />
keys to encrypt the ISAKMP SA when establishing the IPsec SAs. Additionally, D-H is also<br />
used to generate shared secret keys to be used in the ciphers specified in the IPsec transforms,<br />
which are then used in conjunction with the D-H keys by the IPsec to encrypt and decrypt the<br />
data passes through the IPsec VPN tunnel.<br />
- IPsec uses a data integrity algorithm called Hash-based Message Authentication Code<br />
(HMAC) that adds a hash to the message to ensure data integrity. The hash guarantees the<br />
integrity of the original message. If the transmitted hash matches the received hash, the message<br />
is considered has not been tampered.<br />
- IPsec uses the following 2 HMAC algorithms:<br />
Message Digest Algorithm 5<br />
(MD5)<br />
Secure Hash Algorithm 1<br />
(SHA-1)<br />
Uses a 128-bit shared secret key. The message and 128-bit<br />
shared secret key are combined and run through the MD5 hash<br />
algorithm, producing a 128-bit hash. This hash is then added<br />
to the original message and sent to the destination host.<br />
Uses a 160-bit shared secret key. The message and 160-bit<br />
shared secret key are combined and run through the SHA-1<br />
hash algorithm, producing a 160-bit hash. This hash is then<br />
added to the original message and sent to the destination host.<br />
- Below lists the 2 modes of IPsec operation:<br />
Transport Only the payload of the IP packet is encrypted and/or authenticated. The routing is<br />
intact, as the IP header is neither modified nor encrypted. It is used for host-to-host<br />
or end-to-end communications (end systems perform the security processing).<br />
Tunnel The entire IP packet is encrypted and/or authenticated. The original packet is<br />
encapsulated entirely into a new packet with a new set of source and destination IP<br />
addresses for routing to work. It is used for network-to-network or portal-to-portal<br />
communications (gateways or routers perform the security processing). It is the<br />
traditional and default mode of IPsec VPNs.<br />
- The Tunnel mode is most commonly used to secure existing IP traffic for communication<br />
between end systems on networks connected to IPsec-enabled routers. With routers or VPN<br />
endpoints performing the IPsec encryption, no changes are required to the software and drivers<br />
on the end systems – the IPsec implementation is transparent to end systems.<br />
298<br />
Copyright © 2008 Yap Chin Hoong<br />
yapchinhoong@hotmail.com