Handover mechanisms in next generation heterogeneous wireless ...
Handover mechanisms in next generation heterogeneous wireless ...
Handover mechanisms in next generation heterogeneous wireless ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
PROXY BASED AUTHENTICATION LOCALISATION SCHEME FOR HANDOVER<br />
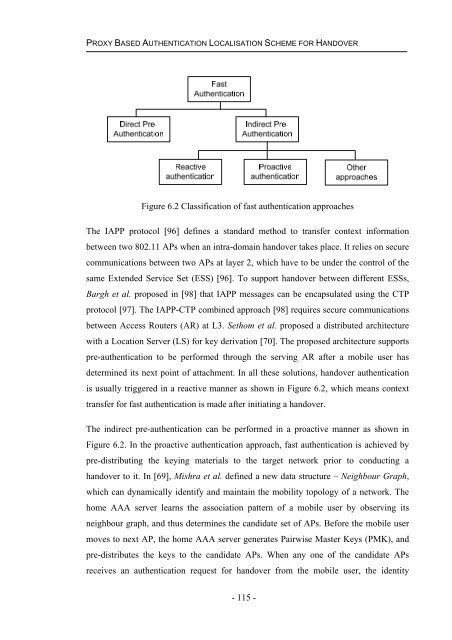
Figure 6.2 Classification of fast authentication approaches<br />
The IAPP protocol [96] def<strong>in</strong>es a standard method to transfer context <strong>in</strong>formation<br />
between two 802.11 APs when an <strong>in</strong>tra-doma<strong>in</strong> handover takes place. It relies on secure<br />
communications between two APs at layer 2, which have to be under the control of the<br />
same Extended Service Set (ESS) [96]. To support handover between different ESSs,<br />
Bargh et al. proposed <strong>in</strong> [98] that IAPP messages can be encapsulated us<strong>in</strong>g the CTP<br />
protocol [97]. The IAPP-CTP comb<strong>in</strong>ed approach [98] requires secure communications<br />
between Access Routers (AR) at L3. Sethom et al. proposed a distributed architecture<br />
with a Location Server (LS) for key derivation [70]. The proposed architecture supports<br />
pre-authentication to be performed through the serv<strong>in</strong>g AR after a mobile user has<br />
determ<strong>in</strong>ed its <strong>next</strong> po<strong>in</strong>t of attachment. In all these solutions, handover authentication<br />
is usually triggered <strong>in</strong> a reactive manner as shown <strong>in</strong> Figure 6.2, which means context<br />
transfer for fast authentication is made after <strong>in</strong>itiat<strong>in</strong>g a handover.<br />
The <strong>in</strong>direct pre-authentication can be performed <strong>in</strong> a proactive manner as shown <strong>in</strong><br />
Figure 6.2. In the proactive authentication approach, fast authentication is achieved by<br />
pre-distribut<strong>in</strong>g the key<strong>in</strong>g materials to the target network prior to conduct<strong>in</strong>g a<br />
handover to it. In [69], Mishra et al. def<strong>in</strong>ed a new data structure – Neighbour Graph,<br />
which can dynamically identify and ma<strong>in</strong>ta<strong>in</strong> the mobility topology of a network. The<br />
home AAA server learns the association pattern of a mobile user by observ<strong>in</strong>g its<br />
neighbour graph, and thus determ<strong>in</strong>es the candidate set of APs. Before the mobile user<br />
moves to <strong>next</strong> AP, the home AAA server generates Pairwise Master Keys (PMK), and<br />
pre-distributes the keys to the candidate APs. When any one of the candidate APs<br />
receives an authentication request for handover from the mobile user, the identity<br />
- 115 -