Handover mechanisms in next generation heterogeneous wireless ...
Handover mechanisms in next generation heterogeneous wireless ...
Handover mechanisms in next generation heterogeneous wireless ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
SECURITY FOR HANDOVER ACROSS HETEROGENEOUS WIRELESS NETWORKS<br />
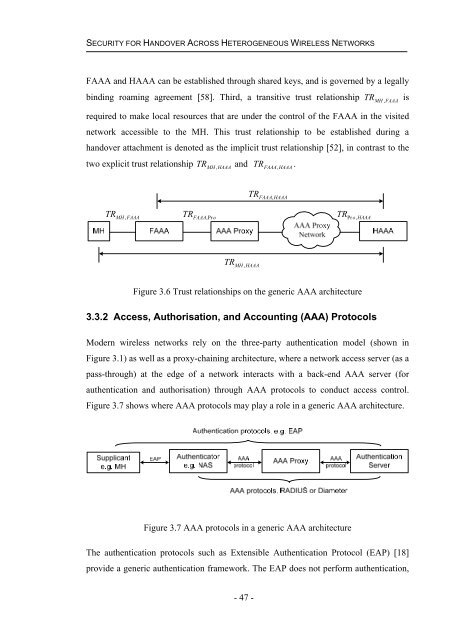
FAAA and HAAA can be established through shared keys, and is governed by a legally<br />
b<strong>in</strong>d<strong>in</strong>g roam<strong>in</strong>g agreement [58]. Third, a transitive trust relationship TR MH , FAAA is<br />
required to make local resources that are under the control of the FAAA <strong>in</strong> the visited<br />
network accessible to the MH. This trust relationship to be established dur<strong>in</strong>g a<br />
handover attachment is denoted as the implicit trust relationship [52], <strong>in</strong> contrast to the<br />
two explicit trust relationship TR MH , HAAA and TR FAAA,<br />
HAAA .<br />
TR MH , FAAA TRFAAA, Pr o<br />
TR Pro,<br />
HAAA<br />
TR MH , HAAA<br />
- 47 -<br />
TR FAAA,<br />
HAAA<br />
Figure 3.6 Trust relationships on the generic AAA architecture<br />
3.3.2 Access, Authorisation, and Account<strong>in</strong>g (AAA) Protocols<br />
Modern <strong>wireless</strong> networks rely on the three-party authentication model (shown <strong>in</strong><br />
Figure 3.1) as well as a proxy-cha<strong>in</strong><strong>in</strong>g architecture, where a network access server (as a<br />
pass-through) at the edge of a network <strong>in</strong>teracts with a back-end AAA server (for<br />
authentication and authorisation) through AAA protocols to conduct access control.<br />
Figure 3.7 shows where AAA protocols may play a role <strong>in</strong> a generic AAA architecture.<br />
Figure 3.7 AAA protocols <strong>in</strong> a generic AAA architecture<br />
The authentication protocols such as Extensible Authentication Protocol (EAP) [18]<br />
provide a generic authentication framework. The EAP does not perform authentication,