Handover mechanisms in next generation heterogeneous wireless ...
Handover mechanisms in next generation heterogeneous wireless ...
Handover mechanisms in next generation heterogeneous wireless ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
PROXY BASED AUTHENTICATION LOCALISATION SCHEME FOR HANDOVER<br />
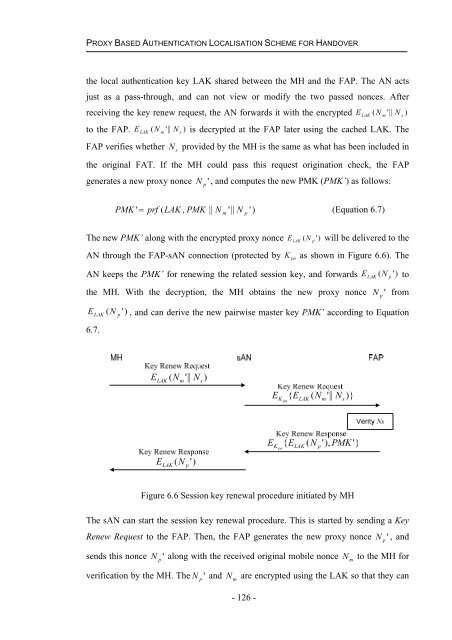
the local authentication key LAK shared between the MH and the FAP. The AN acts<br />
just as a pass-through, and can not view or modify the two passed nonces. After<br />
receiv<strong>in</strong>g the key renew request, the AN forwards it with the encrypted E LAK ( N m '||<br />
N s )<br />
to the FAP. E LAK ( N m '||<br />
N s ) is decrypted at the FAP later us<strong>in</strong>g the cached LAK. The<br />
FAP verifies whether N s provided by the MH is the same as what has been <strong>in</strong>cluded <strong>in</strong><br />
the orig<strong>in</strong>al FAT. If the MH could pass this request orig<strong>in</strong>ation check, the FAP<br />
generates a new proxy nonce N p ' , and computes the new PMK (PMK’) as follows:<br />
PMK ' � prf ( LAK , PMK || N m '||<br />
N p ' )<br />
(Equation 6.7)<br />
The new PMK’ along with the encrypted proxy nonce E ')<br />
will be delivered to the<br />
- 126 -<br />
( p<br />
LAK N<br />
AN through the FAP-sAN connection (protected by K pa as shown <strong>in</strong> Figure 6.6). The<br />
AN keeps the PMK’ for renew<strong>in</strong>g the related session key, and forwards LAK ( p ')<br />
N E to<br />
the MH. With the decryption, the MH obta<strong>in</strong>s the new proxy nonce N p ' from<br />
E LAK ( N p ')<br />
, and can derive the new pairwise master key PMK’ accord<strong>in</strong>g to Equation<br />
6.7.<br />
E<br />
LAK<br />
( Nm<br />
'||<br />
Ns<br />
)<br />
ELAK<br />
( N p ')<br />
EK pa<br />
{ ELAK<br />
( Nm<br />
'||<br />
N s )}<br />
E LAK p<br />
K pa<br />
{ E ( N '),<br />
PMK '}<br />
Figure 6.6 Session key renewal procedure <strong>in</strong>itiated by MH<br />
The sAN can start the session key renewal procedure. This is started by send<strong>in</strong>g a Key<br />
Renew Request to the FAP. Then, the FAP generates the new proxy nonce N p ' , and<br />
sends this nonce N p ' along with the received orig<strong>in</strong>al mobile nonce N m to the MH for<br />
verification by the MH. The N p ' and N m are encrypted us<strong>in</strong>g the LAK so that they can