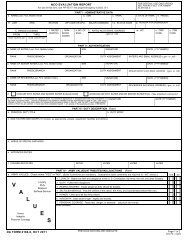
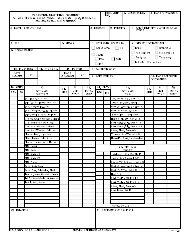
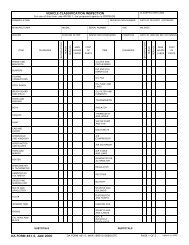
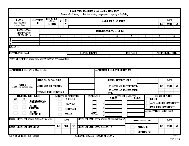
FM 3-34.22 - Army Electronic Publications & Forms - U.S. Army
FM 3-34.22 - Army Electronic Publications & Forms - U.S. Army
FM 3-34.22 - Army Electronic Publications & Forms - U.S. Army
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Chapter 6<br />
adequate time for rehearsals with the gaining or supported unit. The employment of engineer<br />
reconnaissance (discussed in chapter 3) as part of the ISR effort helps generate OBSTINTEL, which<br />
provides the necessary detailed picture of the enemy situation. If breaching operations are anticipated, the<br />
breaching organization is established based on detailed reverse planning (see appendix C). Engineer<br />
priority of effort is toward mobility, with the priority of support to the main effort. Countermobility effort,<br />
primarily through the employment of situational obstacles, is initially directed at supporting the isolation<br />
and fixing of enemy forces and protecting the flanks. Upon seizure of the objective and depending on the<br />
follow-on mission, engineers are prepared to conduct countermobility and survivability operations in<br />
support of a defense, while mobility operations center on clearing obstacles or improving lanes to support<br />
friendly movement. (See <strong>FM</strong> 3-90, <strong>FM</strong> 3-90.5 and <strong>FM</strong> 3-90.6 for more information.)<br />
Exploitation<br />
6-26. An exploitation rapidly follows a successful attack to take advantage of a weakened or collapsed<br />
enemy and seeks to expand an attack to the point where enemy forces have no alternative but to surrender<br />
or flee. It is normally not conducted below the BCT level. The BCT (or higher-level unit) attacks rapidly<br />
over a broad front to prevent the enemy from establishing a defense, organizing an effective rear guard,<br />
withdrawing, or regaining balance. The BCT secures objectives, severs escape routes, and destroys all<br />
enemy forces. The exploitation mission demands a force with a significant mobility advantage over the<br />
enemy.<br />
6-27. Engineers support an exploitation by breaching obstacles to facilitate the maneuver of ground forces,<br />
keeping supply routes open and emplacing situational obstacles to protect the flanks. (See <strong>FM</strong> 3-90, <strong>FM</strong> 3-<br />
90.5, and <strong>FM</strong> 3-90.6 for more information.)<br />
Pursuit<br />
6-28. A pursuit is designed to catch or cut off a hostile force attempting to escape with the aim of<br />
destroying it. Pursuits often follow successful exploitations, but can develop at any point when enemy<br />
forces are beginning to disintegrate or disengage. Unlike an exploitation, which may focus on seizing key<br />
or decisive terrain instead of the enemy force, the pursuit always focuses on destroying the fleeing enemy<br />
force. A pursuit is normally not conducted at the BCT level unless it is augmented with additional aviation<br />
assets or ground maneuver units. When conducted, the goal of a pursuit is to fix the enemy between the<br />
direct-pressure and encircling forces, then, destroy it.<br />
6-29. The direct-pressure and encircling forces require engineers to be forward in movement formations to<br />
quickly breach any obstacles that cannot be bypassed, thus ensuring unimpeded movement. Engineers also<br />
conduct countermobility and survivability tasks in support of the encircling force. Normally, the<br />
commander does not organize specifically for a pursuit ahead of time, although he may plan for a pursuit as<br />
a branch or sequel to his offensive operation. (See <strong>FM</strong> 3-90, <strong>FM</strong> 3-90.5, and <strong>FM</strong> 3-90.6 for more<br />
information.)<br />
FORMS OF MANEUVER<br />
6-30. The maneuver commander selects the form of maneuver based on analysis of mission variables. An<br />
operation may contain several forms of offensive maneuver. For example, a frontal attack to clear enemy<br />
security forces is followed by a penetration to create a gap in enemy defenses, which in turn is followed by<br />
an envelopment to destroy a counterattacking force.<br />
6-31. The five forms of maneuver are—<br />
� Envelopment.<br />
� Turning movement.<br />
� Frontal attack.<br />
� Penetration.<br />
� Infiltration.<br />
6-6 <strong>FM</strong> 3-<strong>34.22</strong> 11 February 2009