Protocols for Secure Communication in Wireless Sensor Networks
Protocols for Secure Communication in Wireless Sensor Networks
Protocols for Secure Communication in Wireless Sensor Networks
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
146 Chapter 5. Multipath <strong>Communication</strong><br />
Frequency<br />
14000<br />
12000<br />
10000<br />
8000<br />
6000<br />
4000<br />
2000<br />
0<br />
0 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22<br />
Common nodes on two tree paths<br />
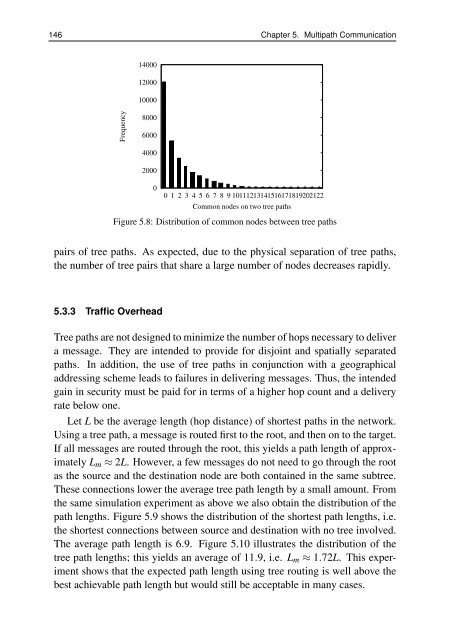
Figure 5.8: Distribution of common nodes between tree paths<br />
pairs of tree paths. As expected, due to the physical separation of tree paths,<br />
the number of tree pairs that share a large number of nodes decreases rapidly.<br />
5.3.3 Traffic Overhead<br />
Tree paths are not designed to m<strong>in</strong>imize the number of hops necessary to deliver<br />
a message. They are <strong>in</strong>tended to provide <strong>for</strong> disjo<strong>in</strong>t and spatially separated<br />
paths. In addition, the use of tree paths <strong>in</strong> conjunction with a geographical<br />
address<strong>in</strong>g scheme leads to failures <strong>in</strong> deliver<strong>in</strong>g messages. Thus, the <strong>in</strong>tended<br />
ga<strong>in</strong> <strong>in</strong> security must be paid <strong>for</strong> <strong>in</strong> terms of a higher hop count and a delivery<br />
rate below one.<br />
Let L be the average length (hop distance) of shortest paths <strong>in</strong> the network.<br />
Us<strong>in</strong>g a tree path, a message is routed first to the root, and then on to the target.<br />
If all messages are routed through the root, this yields a path length of approximately<br />
Lm ≈ 2L. However, a few messages do not need to go through the root<br />
as the source and the dest<strong>in</strong>ation node are both conta<strong>in</strong>ed <strong>in</strong> the same subtree.<br />
These connections lower the average tree path length by a small amount. From<br />
the same simulation experiment as above we also obta<strong>in</strong> the distribution of the<br />
path lengths. Figure 5.9 shows the distribution of the shortest path lengths, i.e.<br />
the shortest connections between source and dest<strong>in</strong>ation with no tree <strong>in</strong>volved.<br />
The average path length is 6.9. Figure 5.10 illustrates the distribution of the<br />
tree path lengths; this yields an average of 11.9, i.e. Lm ≈ 1.72L. This experiment<br />
shows that the expected path length us<strong>in</strong>g tree rout<strong>in</strong>g is well above the<br />
best achievable path length but would still be acceptable <strong>in</strong> many cases.