Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
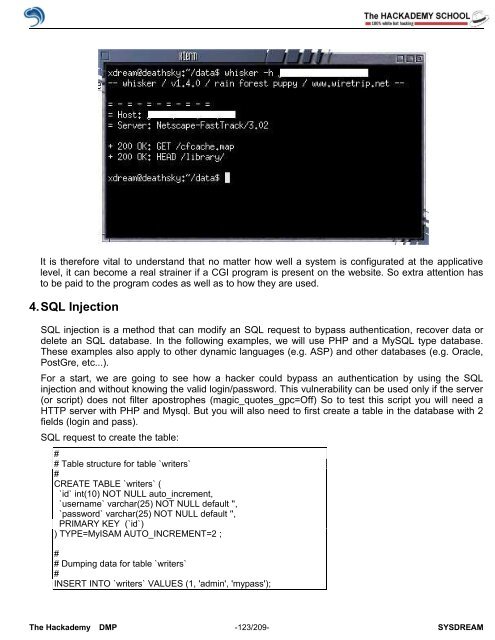
It is therefore vital to understand that no matter how well a system is configurated at the applicative<br />
level, it can become a real strainer if a CGI program is present on the website. So extra attention has<br />
to be paid to the program codes as well as to how they are used.<br />
4.SQL Injection<br />
SQL injection is a method that can modify an SQL request to bypass authentication, recover data or<br />
delete an SQL database. In the following examples, we will use PHP and a MySQL type database.<br />
These examples also apply to other dynamic languages (e.g. ASP) and other databases (e.g. Oracle,<br />
PostGre, etc...).<br />
For a start, we are going to see how a hacker could bypass an authentication by using the SQL<br />
injection and without knowing the valid login/password. This vulnerability can be used only if the server<br />
(or script) does not filter apostrophes (magic_quotes_gpc=Off) So to test this script you will need a<br />
HTTP server with PHP and Mysql. But you will also need to first create a table in the database with 2<br />
fields (login and pass).<br />
SQL request to create the table:<br />
#<br />
# Table structure for table `writers`<br />
#<br />
CREATE TABLE `writers` (<br />
`id` int(10) NOT NULL auto_increment,<br />
`username` varchar(25) NOT NULL default '',<br />
`password` varchar(25) NOT NULL default '',<br />
PRIMARY KEY (`id`)<br />
) TYPE=MyISAM AUTO_INCREMENT=2 ;<br />
#<br />
# Dumping data for table `writers`<br />
#<br />
INSERT INTO `writers` VALUES (1, 'admin', 'mypass');<br />
The <strong>Hack</strong>ademy DMP -123/209- SYSDREAM