Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Let us now display the contents <strong>of</strong> machine B's ARP cache:<br />
Dantes:~# arp -a<br />
arp -a<br />
? (192.168.124.1) at 00:90:4B:77:CC:D1 [ether] on eth0<br />
? (192.168.124.12) at 00:90:4B:77:CC:D1 [ether] on eth0<br />
? (192.168.124.15) at 00:50:BA:5D:35:6C [ether] on eth0<br />
? (192.168.124.10) at 00:50:8D:F9:E2:5E [ether] on eth0<br />
We can see that machine A's address is associated to the hacker machine's MAC address. If we trace<br />
the path taken by a packet from machine B to machine A, we notice that it also passes through<br />
machine C:<br />
Dantes:~# traceroute 192.168.124.1<br />
traceroute 192.168.124.1<br />
traceroute to 192.168.124.1 (192.168.124.1), 30 hops max, 38 byte packets<br />
1 192.168.124.12 (192.168.124.12) 1.093 ms 36.272 ms 1.863 ms<br />
2 192.168.124.1 (192.168.124.1) 3.006 ms 2.242 ms 2.730 ms<br />
Another tool on both Linux and Windows can manage the whole hijacking in a more automatic way:<br />
ettercap. The version used will be the 0.6.0 one, which you will find at:<br />
http://prdownloads.sourceforge.net/ettercap/ettercap-0.6.b.tar.gz?download<br />
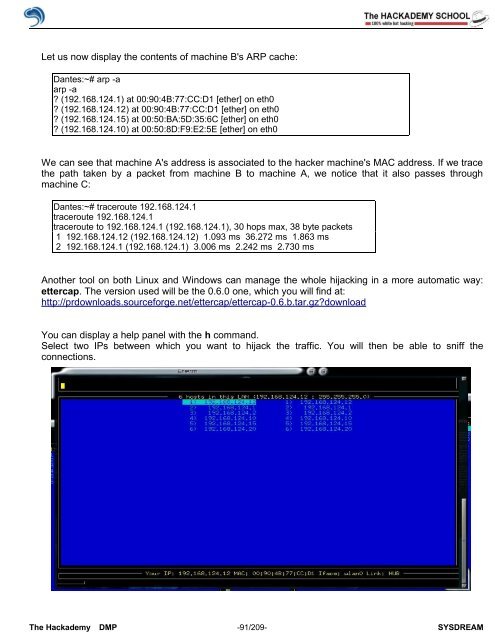
You can display a help panel with the h command.<br />
Select two IPs between which you want to hijack the traffic. You will then be able to sniff the<br />
connections.<br />
The <strong>Hack</strong>ademy DMP -91/209- SYSDREAM