Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
This program is “suidroot”, which means that whoever the user is, it is executed with the rights <strong>of</strong> the<br />
super-user.<br />
This program verifies the user's rights, so it goes without saying that to write in a file with “root” as<br />
owner user whose rights are -rw-r—r--, the executing user must also have super-user rights.<br />
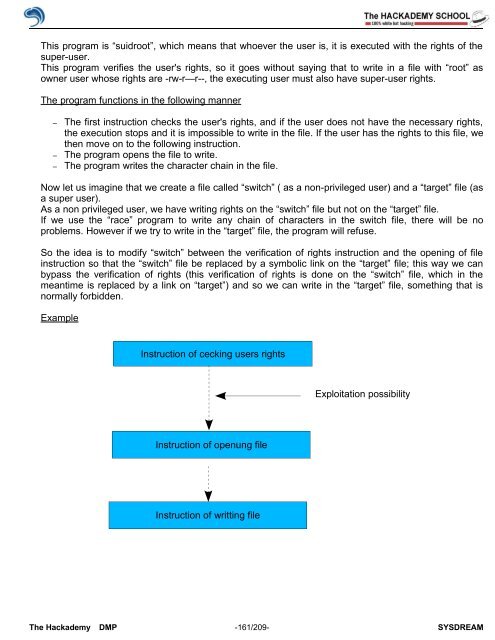
The program functions in the following manner<br />
– The first instruction checks the user's rights, and if the user does not have the necessary rights,<br />
the execution stops and it is impossible to write in the file. If the user has the rights to this file, we<br />
then move on to the following instruction.<br />
– The program opens the file to write.<br />
– The program writes the character chain in the file.<br />
Now let us imagine that we create a file called “switch” ( as a non-privileged user) and a “target” file (as<br />
a super user).<br />
As a non privileged user, we have writing rights on the “switch” file but not on the “target” file.<br />
If we use the “race” program to write any chain <strong>of</strong> characters in the switch file, there will be no<br />
problems. However if we try to write in the “target” file, the program will refuse.<br />
So the idea is to modify “switch” between the verification <strong>of</strong> rights instruction and the opening <strong>of</strong> file<br />
instruction so that the “switch” file be replaced by a symbolic link on the “target” file; this way we can<br />
bypass the verification <strong>of</strong> rights (this verification <strong>of</strong> rights is done on the “switch” file, which in the<br />
meantime is replaced by a link on “target”) and so we can write in the “target” file, something that is<br />
normally forbidden.<br />
Example<br />
Instruction <strong>of</strong> cecking users rights<br />
Instruction <strong>of</strong> openung file<br />
Instruction <strong>of</strong> writting file<br />
Exploitation possibility<br />
The <strong>Hack</strong>ademy DMP -161/209- SYSDREAM