Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
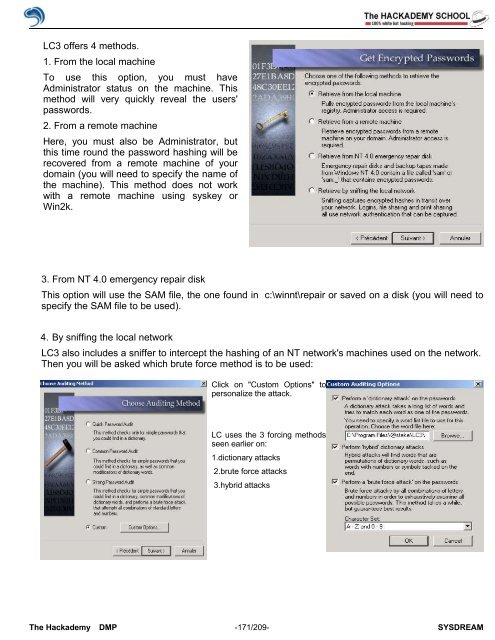
LC3 <strong>of</strong>fers 4 methods.<br />
1. From the local machine<br />
To use this option, you must have<br />
Administrator status on the machine. This<br />
method will very quickly reveal the users'<br />
passwords.<br />
2. From a remote machine<br />
Here, you must also be Administrator, but<br />
this time round the password hashing will be<br />
recovered from a remote machine <strong>of</strong> your<br />
domain (you will need to specify the name <strong>of</strong><br />
the machine). This method does not work<br />
with a remote machine using syskey or<br />
Win2k.<br />
3. From NT 4.0 emergency repair disk<br />
This option will use the SAM file, the one found in c:\winnt\repair or saved on a disk (you will need to<br />
specify the SAM file to be used).<br />
4. By sniffing the local network<br />
LC3 also includes a sniffer to intercept the hashing <strong>of</strong> an NT network's machines used on the network.<br />
Then you will be asked which brute force method is to be used:<br />
Click on "Custom Options" to<br />
personalize the attack.<br />
LC uses the 3 forcing methods<br />
seen earlier on:<br />
1.dictionary attacks<br />
2.brute force attacks<br />
3.hybrid attacks<br />
The <strong>Hack</strong>ademy DMP -171/209- SYSDREAM