Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
However, do check in the start files <strong>of</strong> the computer what the situation is and cancel the call to this pilot<br />
if it does exist.<br />
Logical bombs: Some programs that do not have the ability to reproduce can still cause serious<br />
damage. S<strong>of</strong>tware <strong>of</strong>ficially presented as a game can include a destructive function triggered during a<br />
precise event or at a pre-determined date. Sometimes, it is only an innocent prank. However, some<br />
programmers are real sadists, even if this is rare.<br />
Trojan horses: Trojan horses are an under-category <strong>of</strong> logical bombs. They do not have an immediate<br />
destructive aim: their task is limited to espionage. They gather confidential information on the user <strong>of</strong><br />
the PC into which they have entered and transmit these to their creator. Some horses' mission is to<br />
establish an access (for example through a network) to the infected computer. The Internet being more<br />
and more used in commercial transactions, many new Trojan horses have been circulated.<br />
2. Trojans<br />
There are different sorts <strong>of</strong> hidden gateways. The best well-known remains the trojan. A trojan is<br />
s<strong>of</strong>tware executed without the user's knowledge. It will start to listen to a port on the system and wait<br />
for adapted clients. Quite <strong>of</strong>ten a trojan kit is made up <strong>of</strong> a client s<strong>of</strong>tware, which is normally harmless<br />
for the user, and an executable server. Many trojans are available on the Internet. As they are for the<br />
majority referenced by antiviruses and conceived for Windows, a hacker attacking a Linux machine or<br />
wishing to use more discreet s<strong>of</strong>tware will have to find alternative solutions.<br />
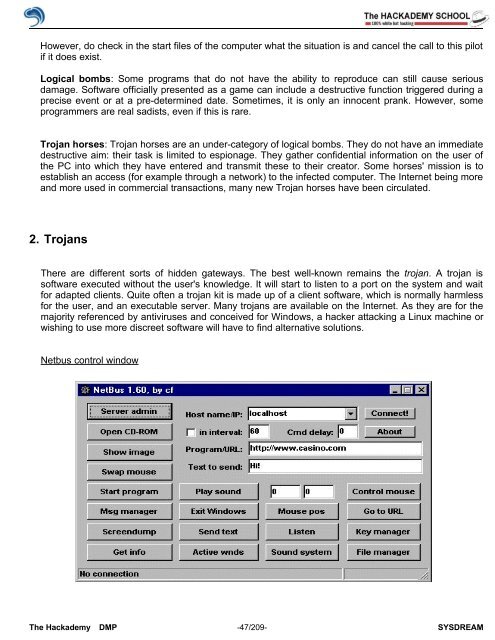
Netbus control window<br />
The <strong>Hack</strong>ademy DMP -47/209- SYSDREAM