Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
1.Network Sniffing<br />
A) Theoretical Approach<br />
Sniffing is a spying technique which consists in copying the information contained in network packets<br />
without modifying their transportation or their shape.<br />
When an A machine contacts a C machine, data will transit through an intermediate machine, a B<br />
machine.<br />
A -----> B -----> C<br />
To reach C, A must have the packet transit through B. B could be controlled by a hacker, and this<br />
hacker could then maliciously pick up the data transiting between A and C and make a copy <strong>of</strong> it for<br />
later analysis.<br />
Sniffing makes it possible to pick up the data that makes up the network packets, i.e. the different<br />
options and variables incremented in the packets (Source IP address, Destination IP address, Flags,<br />
etc.), as well as usual data (web pages' source codes, logins and passwords, commands sent to a<br />
server, etc.) The reason sniffing exists is the security weakness <strong>of</strong> the vast majority <strong>of</strong> protocols. The<br />
confidentiality <strong>of</strong> data transmitted with the most common protocols (TCP, HTTP, FTP, SMTP, ...) is not<br />
ensured because these communications are not encrypted. In some network environments, it is not<br />
even necessary to be part <strong>of</strong> the relay system (router, gateway, etc.) to undertake network sniffing...<br />
Networks environments : simplicity and limits <strong>of</strong> sniffing<br />
In some network environments, it is not necessary to be in control <strong>of</strong> the relay machine to spy on the<br />
whole data flow. This is for example the case for network architectures structured around a HUB. The<br />
whole network created around a hub is vulnerable to a Sniffing-type technique. All packets emitted on<br />
the network are broadcast to all the systems present. By analysing the destination MAC address, the<br />
system receiving the packet can decide if this packet is destined to it or if it must be dropped.<br />
However, on a hub network, this method is limited to zones belonging to the same network segment.<br />
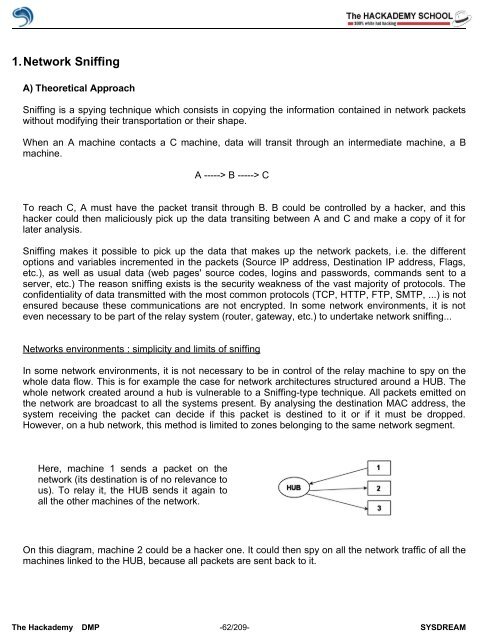
Here, machine 1 sends a packet on the<br />
network (its destination is <strong>of</strong> no relevance to<br />
us). To relay it, the HUB sends it again to<br />
all the other machines <strong>of</strong> the network.<br />
On this diagram, machine 2 could be a hacker one. It could then spy on all the network traffic <strong>of</strong> all the<br />
machines linked to the HUB, because all packets are sent back to it.<br />
The <strong>Hack</strong>ademy DMP -62/209- SYSDREAM