You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
We will simultaneously launch the packets emissions for a better analysis <strong>of</strong> results.<br />
First terminal; emission <strong>of</strong> spo<strong>of</strong>ed packets to server S.<br />
Here, C asks for connections to S. The ID is incremented <strong>of</strong> +1 at each sending.<br />
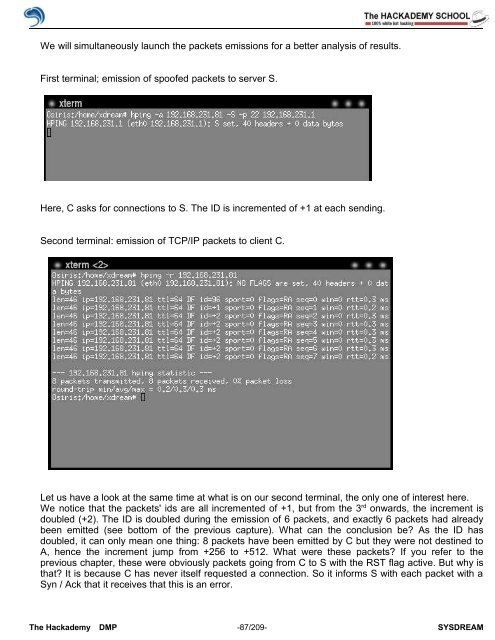
Second terminal: emission <strong>of</strong> TCP/IP packets to client C.<br />
Let us have a look at the same time at what is on our second terminal, the only one <strong>of</strong> interest here.<br />
We notice that the packets' ids are all incremented <strong>of</strong> +1, but from the 3 rd onwards, the increment is<br />
doubled (+2). The ID is doubled during the emission <strong>of</strong> 6 packets, and exactly 6 packets had already<br />
been emitted (see bottom <strong>of</strong> the previous capture). What can the conclusion be? As the ID has<br />
doubled, it can only mean one thing: 8 packets have been emitted by C but they were not destined to<br />
A, hence the increment jump from +256 to +512. What were these packets? If you refer to the<br />
previous chapter, these were obviously packets going from C to S with the RST flag active. But why is<br />
that? It is because C has never itself requested a connection. So it informs S with each packet with a<br />
Syn / Ack that it receives that this is an error.<br />
The <strong>Hack</strong>ademy DMP -87/209- SYSDREAM