Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
To dialogue with C and to force it to reveal its id, two solutions can be imagined:<br />
1) We try to initialize a connection on an active port <strong>of</strong> machine C by sending packets with the Syn flag<br />
activated (this is very important, otherwise the machine will not answer). The machine will then<br />
answer by sending packets with activated Syn and Ack flags.<br />
2) We send packets to a closed port (there is no need to activate a flag). The machine will believe it is<br />
an error and will send response packets with Ack and Reset flags activated.<br />
Which is the best method? Both actually work very well, however the first one presents two major<br />
disadvantages: if we want to follow the same logic we have had since the beginning, choosing a<br />
machine C with even only one open port is ridiculous (in this case it is a server and the risks <strong>of</strong><br />
establishing a connection with anyone other than A are high). Also, sending a flood <strong>of</strong> connection<br />
requests to C on a specific port could be unfavorably interpreted by a watchful administrator who<br />
checks his logs (he could believe it is a syn flooding or a syn scanning).<br />
We are therefore going to forge packets according to the second method, and to do this we will use<br />
hping. Hping, just like Nemesis, is a tcp/ip packet forger. Why choose hping? Because hping has an<br />
interesting function that allows it to log on console <strong>of</strong> answers to packets emitted via hping.<br />
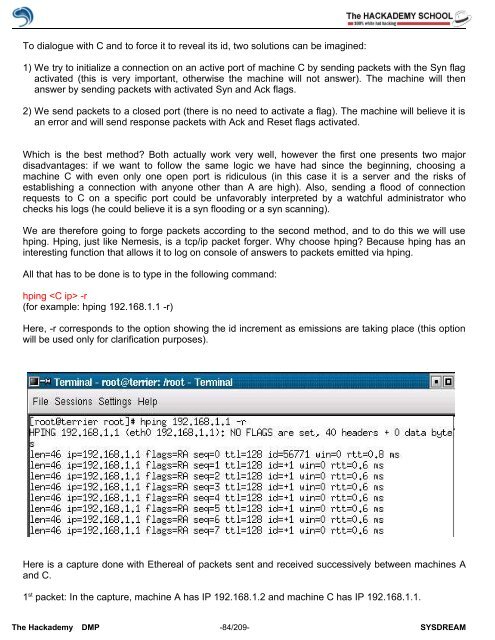
All that has to be done is to type in the following command:<br />
hping -r<br />
(for example: hping 192.168.1.1 -r)<br />
Here, -r corresponds to the option showing the id increment as emissions are taking place (this option<br />
will be used only for clarification purposes).<br />
Here is a capture done with Ethereal <strong>of</strong> packets sent and received successively between machines A<br />
and C.<br />
1 st packet: In the capture, machine A has IP 192.168.1.2 and machine C has IP 192.168.1.1.<br />
The <strong>Hack</strong>ademy DMP -84/209- SYSDREAM