Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
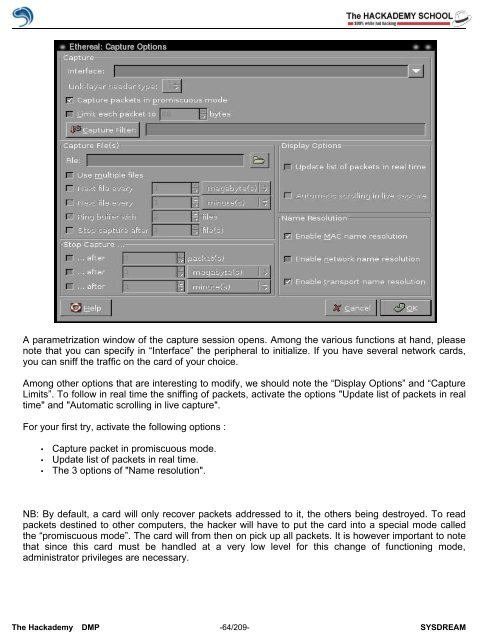
A parametrization window <strong>of</strong> the capture session opens. Among the various functions at hand, please<br />
note that you can specify in “Interface” the peripheral to initialize. If you have several network cards,<br />
you can sniff the traffic on the card <strong>of</strong> your choice.<br />
Among other options that are interesting to modify, we should note the “Display Options” and “Capture<br />
Limits”. To follow in real time the sniffing <strong>of</strong> packets, activate the options "Update list <strong>of</strong> packets in real<br />
time" and "Automatic scrolling in live capture".<br />
For your first try, activate the following options :<br />
• Capture packet in promiscuous mode.<br />
• Update list <strong>of</strong> packets in real time.<br />
• The 3 options <strong>of</strong> "Name resolution".<br />
NB: By default, a card will only recover packets addressed to it, the others being destroyed. To read<br />
packets destined to other computers, the hacker will have to put the card into a special mode called<br />
the “promiscuous mode”. The card will from then on pick up all packets. It is however important to note<br />
that since this card must be handled at a very low level for this change <strong>of</strong> functioning mode,<br />
administrator privileges are necessary.<br />
The <strong>Hack</strong>ademy DMP -64/209- SYSDREAM