Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Security</strong><br />
There are a great number <strong>of</strong> s<strong>of</strong>twares able to crack any number <strong>of</strong> protected file (pwl, sam, zip,<br />
excel, word, etc...).<br />
• It is therefore important to always choose a password with a maximum <strong>of</strong> alphabetical<br />
characters, numbers and special characters (to increase to the maximum the amount <strong>of</strong> time<br />
that the hacker would take to find your password).<br />
• Change password as <strong>of</strong>ten as possible. The hacker won't have the time to crack your<br />
password if it changes all the time).<br />
• Use a BIOS password to have access to Setup and to the operating system and change the<br />
boot sequence to avoid having to boot from a disk.<br />
• Avoid asking Windows to save your passwords (Internet access, messaging, etc...)<br />
• For those who have never used a Firewall, install simple to use s<strong>of</strong>tware such as ZoneAlarm,<br />
as this will enable you to detect any intrusion on your machine and to block certain ports or<br />
protocols. You should also install an antivirus.<br />
• Update your operating system, as well as your s<strong>of</strong>tware, as <strong>of</strong>ten as possible.<br />
• Do not always use the same password for different identifications.<br />
• Always change the password by default <strong>of</strong> all the services installed on your machine.<br />
• Do not store any SAM files on its NT system, which is accessible to all.<br />
2.System spying<br />
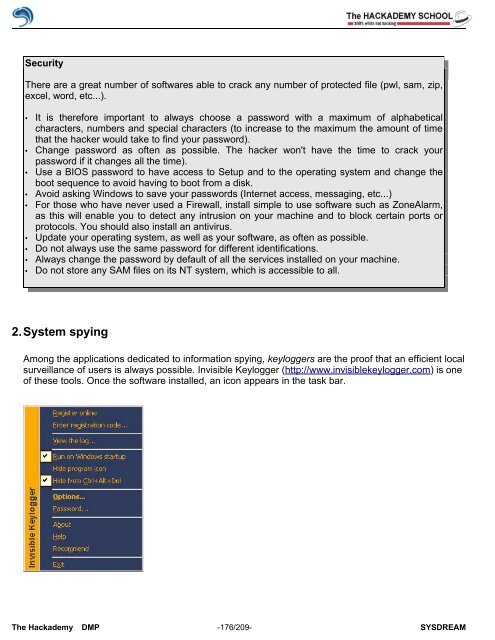
Among the applications dedicated to information spying, keyloggers are the pro<strong>of</strong> that an efficient local<br />
surveillance <strong>of</strong> users is always possible. Invisible Keylogger (http://www.invisiblekeylogger.com) is one<br />
<strong>of</strong> these tools. Once the s<strong>of</strong>tware installed, an icon appears in the task bar.<br />
The <strong>Hack</strong>ademy DMP -176/209- SYSDREAM